A contemporary record from Palo Alto Networks’s Unit 42 exposes the chronic and evolving danger of DNS hijacking, a stealthy tactic cybercriminals use to reroute web visitors. By leveraging passive DNS research, the cybersecurity corporate additionally supplied real-world examples of new DNS hijacking assaults — highlighting the urgency of countering this hidden threat.
What is DNS hijacking?
DNS hijacking comes to editing the responses from focused DNS servers, redirecting customers to attacker-controlled servers as a substitute of the reliable ones they intend to succeed in.
DNS hijacking will also be accomplished in different techniques:
- Gaining keep watch over of the area proprietor’s account, offering get entry to to DNS server settings: In this state of affairs, the attacker possesses legitimate person credentials with the authority to at once exchange the DNS server configuration. The attacker may even have legitimate credentials for the area registrar or DNS provider supplier and alter the configuration.
- DNS cache poisoning: The attacker impersonates a DNS nameserver and forges a answer, resulting in attacker-controlled content material as a substitute of the reliable one.
- Man-in-the-Middle assault: The attacker intercepts the person’s DNS queries and offers effects that redirect the sufferer to the attacker-controlled content material. This simplest works if the attacker is in keep watch over of a device implicated within the DNS question/resolution procedure.
- Modifying DNS-related device recordsdata, such because the host report in Microsoft Windows programs. If the attacker has get entry to to that native report, it’s conceivable to redirect the person to attacker-controlled content material.
Attackers normally use DNS hijacking to redirect customers to phishing web pages that glance very similar to the supposed web pages or to contaminate the customers with malware.
Detecting DNS hijacking with passive DNS
The Unit 42 record described a strategy to come across DNS hijacking by way of passive DNS research.
What is passive DNS?
Passive DNS describes terabytes of historic DNS queries. In addition to the area title and the DNS report sort, passive DNS information normally comprise a “first seen” and a “last seen” timestamp. These information permit customers to track the IP addresses a website has directed customers to through the years.
For an access to look in passive DNS, it should be queried by way of a device whose DNS queries are recorded by way of passive DNS programs. This is why probably the most complete passive DNS knowledge normally comes from suppliers with top question volumes, akin to ISPs or corporations with intensive buyer bases. Subscribing to a passive DNS supplier is regularly really helpful, as they accumulate extra DNS queries than the common corporate, providing a extra whole view than native DNS queries on my own.
SEE: Everything You Need to Know in regards to the Malvertising Cybersecurity Threat (roosho Premium)
Detecting DNS hijacking
Palo Alto Network’s means for detecting DNS hijacking starts by way of figuring out never-seen-before DNS information, as attackers regularly create new information to redirect customers. Never-seen-before domains are excluded from detection as a result of they lack enough historic knowledge. Invalid information also are got rid of at this step.
The DNS information are then analyzed the use of passive DNS and geolocation knowledge in keeping with 74 options. According to the record, “some features compare the historical usage of the new IP address to the old IP address of the domain name in the new record.” The function is to come across anomalies that would point out a DNS hijack operation. A machine-learning fashion then supplies a likelihood ranking in keeping with the research.
WHOIS information also are checked to stop a website from being re-registered, which normally leads to an entire IP cope with exchange that may be detected as DNS hijack.
Finally, lively navigations are performed at the domain names’ IP addresses and HTTPS certificate. Identical effects point out false positives and will due to this fact be excluded from DNS hijacking operations.
DNS hijack statistics
From March 27 to Sept. 21 2024, researchers processed 29 billion new information, 6,729 of which have been flagged as DNS hijacking. This led to a median of 38 DNS hijack information in keeping with day.
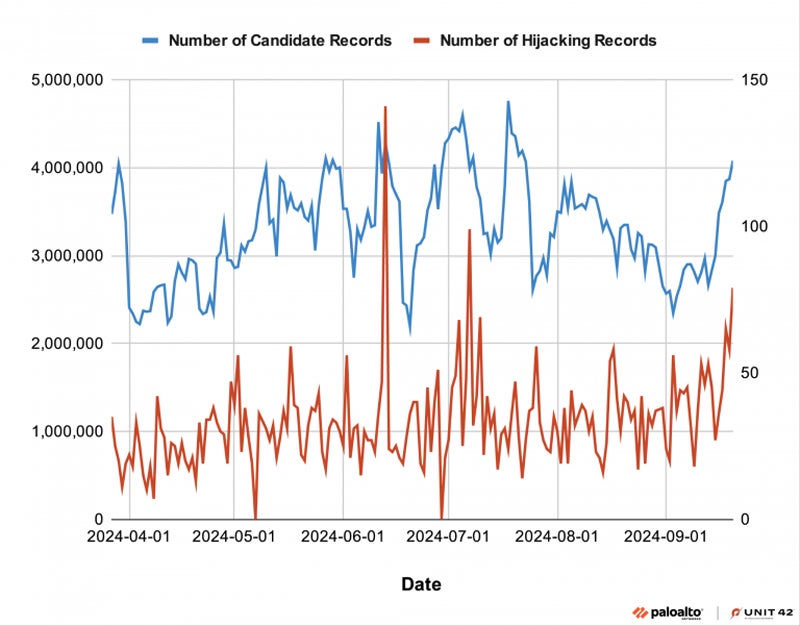
Unit 42 signifies that cybercriminals have hijacked domain names to host phishing content material, deface web pages, or unfold illicit content material.
DNS hijacking: Real-world examples
Unit 42 has considered a couple of DNS hijack circumstances within the wild, most commonly for cybercrime functions. Yet it’s also conceivable to make use of DNS hijacking for cyberespionage.
Hungarian political occasion ends up in phishing
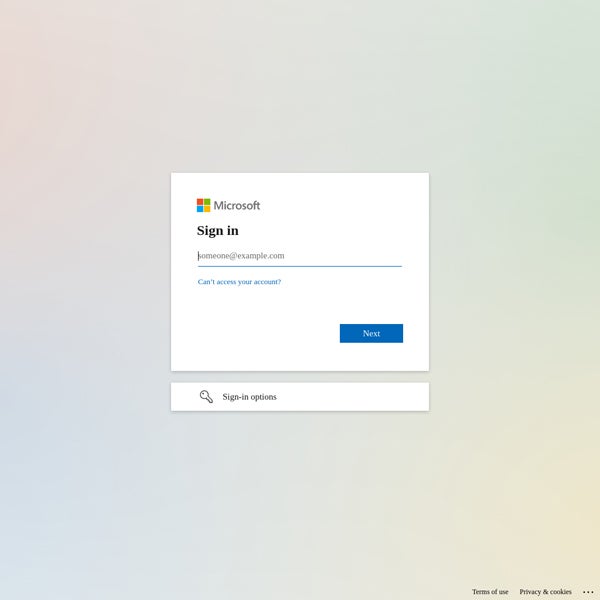
One of the most important political opposition teams to the Hungarian executive, the Democratic Coalition (DK), has been hosted at the similar subnet of IP addresses in Slovakia since 2017. In January 2024, researchers detected a metamorphosis within the DK’s website online, which resolved to a brand new German IP cope with, resulting in a Microsoft login web page as a substitute of the political occasion’s standard information web page.
US corporate defaced
In May 2024, two domain names of a number one U.S. application control corporate had been hijacked. The FTP provider, which has ended in the similar IP cope with since 2014, modified. The DNS nameserver used to be hijacked the use of the attacker-controlled ns1.csit-host.com.
According to the analysis, the attackers extensively utilized the similar nameservers to hijack different web pages in 2017 and 2023. The function of the operation used to be to turn a defaced web page from an activist team.
How corporations can offer protection to themselves from this danger
To offer protection to from those threats, the record advised that organizations:
- Deploy multi-factor authentication to get entry to their DNS registrar accounts. Establishing a whitelist of IP addresses allowed to get entry to DNS settings could also be a good suggestion.
- Leverage a DNS registrar that helps DNSSEC. This protocol provides a layer of safety by way of digitally signing DNS communications, making it harder to intercept and spoof knowledge for danger actors.
- Use networking equipment that evaluate DNS queries effects from third-party DNS servers — akin to the ones from ISPs — to the DNS queries effects received when the use of the corporate’s standard DNS server. A mismatch may point out a metamorphosis in DNS settings, which may well be a DNS hijacking assault.
In addition, all {hardware}, akin to routers, should have up-to-date firmware, and all tool should be up-to-date and patched to steer clear of being compromised by way of commonplace vulnerabilities.
Disclosure: I paintings for Trend Micro, however the perspectives expressed on this article are mine.






No Comment! Be the first one.