A brand new document from Mandiant, a part of Google Cloud, finds {that a} financially motivated danger actor named UNC5537 accrued and exfiltrated information from about 165 organizations’ Snowflake buyer cases. Snowflake is a cloud information platform used for storing and inspecting massive volumes of knowledge.
The danger actor controlled to get get right of entry to to those information via triggering credentials that have been up to now stolen via infostealer malware or bought from different cybercriminals.
According to Mandiant, the danger actor UNC5537 advertises sufferer information on the market on cybercrime boards and makes an attempt to extort lots of the sufferers. When the knowledge is bought, any cybercriminal would possibly purchase this knowledge for various functions comparable to cyber espionage, aggressive intelligence or extra financially-oriented fraud.
How have been some Snowflake customers focused for this information robbery and extortion?
A joint commentary equipped via Snowflake, Mandiant and cybersecurity corporate CrowdStrike signifies there’s no proof suggesting the fraudulent task can be led to via a vulnerability, misconfiguration or breach of Snowflake’s platform. There could also be no proof the task would had been led to via compromised credentials from present or previous Snowflake workers.
Instead, proof displays the attackers acquired credentials from more than one infostealer malware campaigns that inflamed non-Snowflake owned methods. The danger actor then won get right of entry to to the affected accounts, which allowed the exfiltration of an important quantity of shopper information from the respective Snowflake buyer cases.
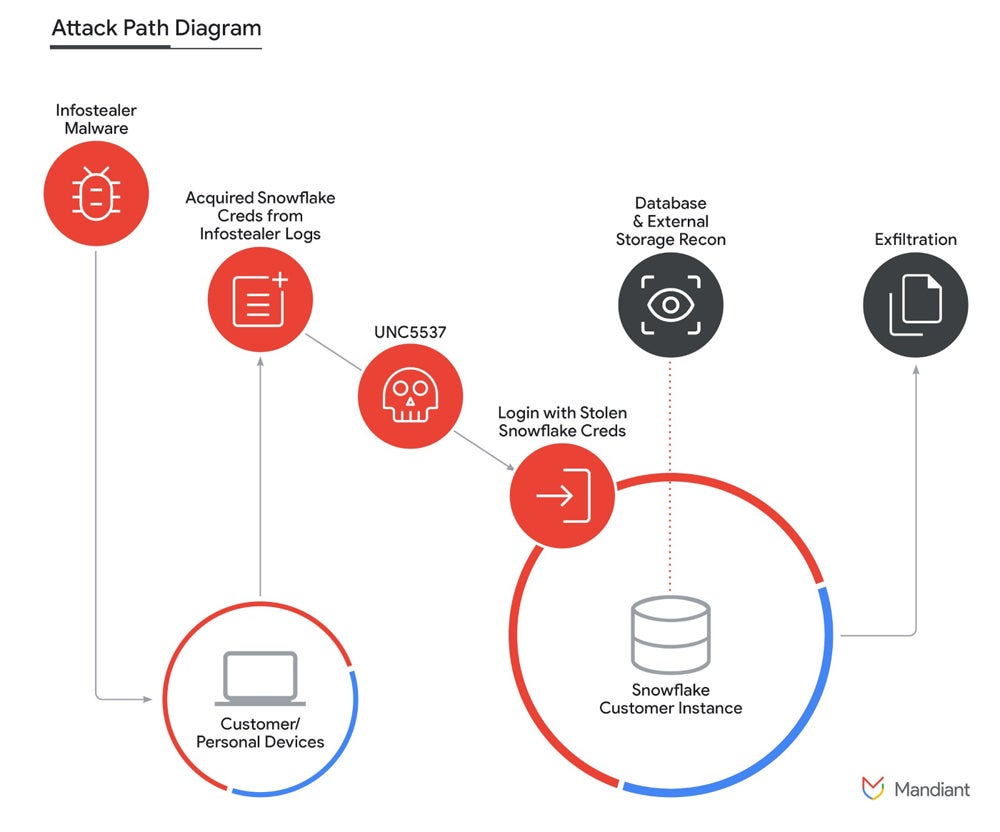
Mandiant researchers said the vast majority of the credentials utilized by UNC5537 have been to be had from ancient infostealer malware; a few of the ones credentials date again to November 2020 however have been nonetheless usable. Different infostealer malware households have been chargeable for the credentials robbery — essentially the most used ones being Vidar, Risepro, Redline, Racoon Stealer, Lumma and Metastealer.
According to Mandiant and Snowflake, no less than 79.7% of the accounts leveraged via the danger actor had prior credential publicity.
Mandiant additionally reported the preliminary compromise of infostealer malware passed off on contractor methods that have been extensively utilized for private actions, together with gaming and downloads of pirated tool, which is a sturdy vector for spreading infostealers.
How did UNC5537 download the stolen credentials?
As reported, the danger actor acquired credentials from a lot of infostealer malware, but UNC5537 additionally leveraged credentials that have been up to now bought.
While no more information is equipped via Mandiant, it’s affordable to suppose the ones credentials have been purchased in a single or a number of cybercriminal underground marketplaces at once to so-called Initial Access Brokers, which can be a class of cybercriminals who promote stolen company get right of entry to to different fraudsters.
As written via Mandiant in its document, “the underground infostealer economy is also extremely robust, and large lists of stolen credentials exist both for free and for purchase inside and outside of the dark web.” Mandiant additionally reported that, in 2023, 10% of general intrusions started with stolen credentials, representing the fourth maximum notable preliminary intrusion vector.
What used to be the preliminary get right of entry to and knowledge exfiltration strategies on this Snowflake assault?
In this assault marketing campaign, the preliminary get right of entry to to Snowflake buyer cases frequently passed off by way of the local consumer interface obtainable from the internet (Snowflake SnowSight) or from the command-line interface device equipped via Snowflake (SnowSQL). An further attacker-named device referred to as “rapeflake” and tracked below FROSTBITE via Mandiant has been used to accomplish reconnaissance in opposition to Snowflake cases.
FROSTBITE exists in no less than two variations: one the usage of .NET to have interaction with the Snowflake .NET driving force, and one model the usage of Java to have interaction with the Snowflake JDBC driving force. The device permits the attackers to accomplish SQL actions comparable to checklist customers, present roles, present IP addresses, consultation IDs and organizations’ names.
A public device for managing databases, DBeaver Ultimate, has additionally been utilized by the danger actor to run queries at the Snowflake cases.
Using SQL queries, the danger actor used to be ready to exfiltrate knowledge from databases. Once fascinating information used to be discovered, it used to be compressed as GZIP the usage of the “COPY INTO” command to scale back the dimensions of the knowledge to be exfiltrated.
The attacker basically used Mullvad and Private Internet Access VPN products and services to get right of entry to the sufferers’ Snowflake cases. A moldovan VPS supplier, ALEXHOST SRL, used to be extensively utilized for information exfiltration. The danger actor saved sufferer information on a number of world VPS suppliers, in addition to at the cloud garage supplier MEGA.
What organizations are in danger?
The assault marketing campaign seems to be a focused marketing campaign aimed toward Snowflake customers with single-factor authentication. All customers with multifactor authentication are secure from this assault marketing campaign and weren’t focused.
In addition, the impacted Snowflake buyer cases didn’t have permit lists in position to just permit connections from relied on places.
Tips from Snowflake on how to offer protection to your small business from this cybersecurity danger
Snowflake revealed knowledge on detecting and combating unauthorized consumer get right of entry to.
The corporate equipped a listing of just about 300 suspicious IP addresses utilized by the danger actor and shared a question to spot get right of entry to from the suspect IP addresses. The corporate additionally equipped a question to spot using the “rapeflake” and “DBeaver Ultimate” equipment. Any consumer account returning effects from the ones queries will have to instantly be disabled.
Security hardening is extremely really helpful via Snowflake:
- Enforce MFA for customers.
- Set up account-level and user-level community insurance policies for extremely credentialed customers/products and services accounts.
- Review account parameters to limit information exportation from Snowflake accounts.
- Monitor Snowflake accounts for unauthorized privilege escalation or configuration adjustments and examine any of the ones occasions.
Additionally, it is suggested to have all tool and running methods up-to-the-minute and patched to steer clear of being compromised via a commonplace vulnerability, which would possibly result in credentials leak.
Security answers want to be deployed on each endpoint to stop infostealer an infection.
It could also be prompt to boost consciousness on laptop safety and educate body of workers to come across and document suspicious cybersecurity occasions.
Disclosure: I paintings for Trend Micro, however the perspectives expressed on this article are mine.






No Comment! Be the first one.