As readers of my earlier desktop Linux DNS article will have the ability to attest, systemd’s control of DNS is advanced. By hanging time into comprehending its complexity, regardless that, we will be able to create nuanced DNS answer behaviors for specialised use instances.
To pick out again up, this installment will get started via fleshing out how systemd-resolved routes queries. From there, I can define methods to configure DNS on a per-link foundation. To shut, I can mirror on why it’s so tricky to get easy, constant, and actionable data in this topic.
Everything in Its Proper Domain
Last time, I made cursory point out that, in systemd-resolved’s configuration, “~.” is a different route-only area that specifies the “default” hyperlink (or world) to make use of for DNS answer. Let’s cross into element.
In systemd-resolved’s cut up DNS, there are two modes of specifying which queries cross to which hyperlinks/world: seek domain names and route-only domain names. Both seek and route-only domain names are set to a website string as a worth (e.g., “linuxinsider.com”). Each hyperlink/world can solely have one area configured, both a route-only or seek area (no longer each).
When a website is submitted for a question, it’s when compared towards all the seek and route-only domain names that experience configured (i.e., non-empty) values.
If (solely) one of the configured seek/route-only area values is located inside the area being queried, this is regarded as a “match,” and the question is distributed to the hyperlink with the matching seek/route-only area.
If a couple of seek/route-only domain names fit, the question is distributed to the hyperlink/world whose seek/route-only area is the longest.
If none of the hunt/route-only domain names fit, all hyperlinks and world get despatched the DNS question. Since the entire level of DNS is that this can be a disbursed however constant machine, they will have to all provide the similar solution, but it surely nonetheless sinks pointless time and compute sources into the question.
Search and route-only domain names are virtually an identical in capability. In my analysis, I didn’t get as transparent a solution as I’d was hoping at the distinction. As the Fedora Magazine article and Gnome Foundation weblog submit point out, and the systemd-resolved guy web page corroborates, the principle difference is in dealing with “single-label” domain names.
With seek domain names, in case you are querying a “single-label” area and not using a “.” characters in it, the question is performed with the hunt area’s worth appended to it. For example, if now we have a seek area for “example.com” configured on a hyperlink, and we question “mail,” the submitted question would cross to that hyperlink and be queried as “mail.example.com.” By implication, we will be able to say that single-label queries are all the time attempted towards all configured seek domain names, and via definition, single-label queries don’t seem to be going to compare any route-only or seek domain names on their very own as a result of they have got no less than one “.” in them.
The different notable difference is how seek and route-only domain names are configured. All configured per-link domain names are seek domain names via default. Prepending a “~” to the area makes it a route-only area.
This brings us to our good friend “~.”. As alluded to within the previous piece, “~.” suits any question that doesn’t fit another route-only or seek domain names. Thinking about it, that is sensible. It is functionally the default as a result of all domain names (excluding single-label) will all the time fit since all of them have “.” in them. But this area fit will all the time be shorter than another conceivable route-only/seek area. Hence, it’s a default.
The querying order and go back prerequisites are much more advanced than this. If you’re demise to grasp the whole lot, crack open the “systemd-resolved” guy web page connected above. But that is actually all we want to perceive systemd-resolved to a realistic stage.
Reassembling All the Split Pieces
Now we’re in a position to know systemd-resolved’s cut up DNS conduct.
To adapt an instance from the Gnome Foundation piece, let’s take the average state of affairs of connecting to a piece VPN. In Linux, VPNs (amongst different networking configurations) can create a digital networking interface. Your pc treats it like another networking interface (e.g., a wi-fi card), however it’s digital (i.e., tool somewhat than {hardware}). Further, systemd-resolved additionally treats this digital networking interface as a hyperlink. Thus, it may have its personal DNS configuration.
On a piece VPN, it’s possible you’ll want to question work-related domain names towards a DNS server at the community around the VPN tunnel. Well-implemented Linux VPN tool might be designed to make the right kind systemd-resolved API calls to configure its hyperlink in systemd-resolved with any route-only or seek area, in addition to any DNS servers it wishes.
As such, let’s say the VPN hyperlink has “ecorp.com” as its seek area, and let’s say that is along with your wi-fi card that has the “~.” route-only area. The result’s that any domain names you question that include “ecorp.com” will cross to the DNS servers set at the VPN hyperlink. All different DNS queries would cross to the wi-fi hyperlink’s servers.
So, what occurs if we go away “~.” out of our wi-fi hyperlink? Domain queries containing “ecorp.com” or single-label queries will serve as the similar as ahead of. However, any domain names no longer matching the VPN hyperlink’s seek area might be queried on all hyperlinks/world. If you don’t need the company VPN to peer the place you’re surfing, that is unwanted.
The Missing Link Files
Although we made up our minds within the previous piece on this collection that if all you need is to override the DNS servers supplied via your get entry to level (AP), converting systemd-resolved’s world configuration is best possible. However, it’s possible you’ll come upon scenarios the place you wish to have to tweak the DNS conduct on a selected hyperlink.
To do this, we flip to systemd-networkd, any other daemon that controls networking conduct. systemd-networkd handles your entire community units in step with its personal defaults, however you’ll be able to give it customized directions. If systemd-networkd unearths information within the /and so forth/systemd/community listing with the right kind filename conventions and report contents, it’s going to do as you inform it.
Besides your required DNS servers, all you wish to have to grasp entering into is the title of your community interface. To view your interfaces, run ip hyperlink. For maximum desktop Linux installations, the one interfaces you’ll most probably in finding are “lo” (“loopback,” a self-reference), a wi-fi interface, and possibly an Ethernet interface.
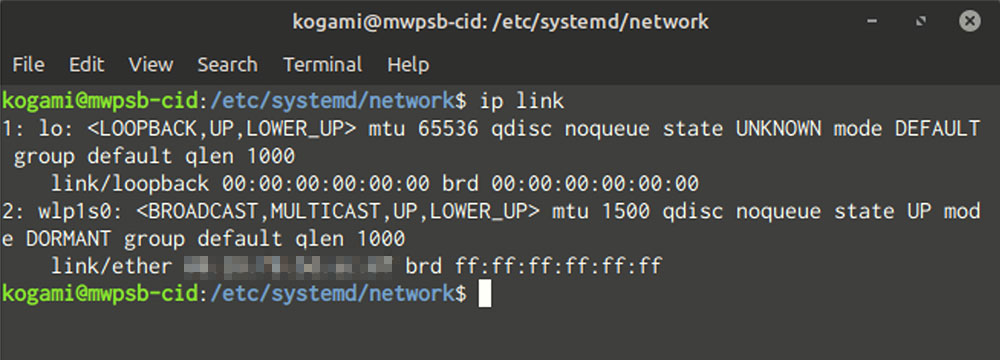
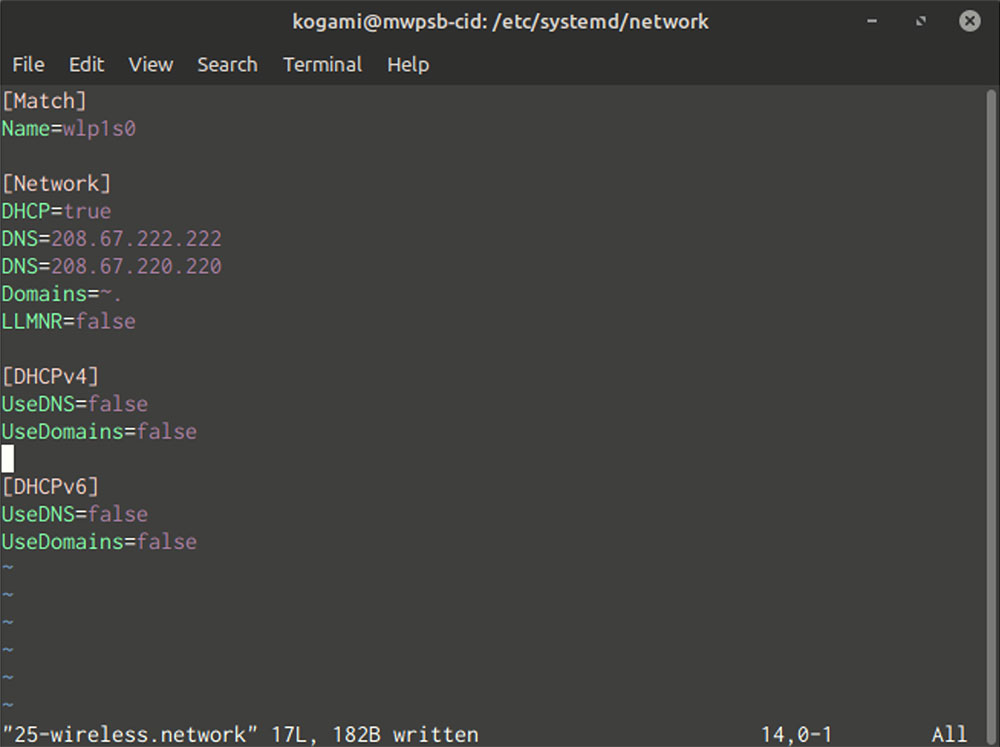
Interface title in hand, create a report to your interface (as superuser) in /and so forth/systemd/community with a filename finishing in “.network”. Set the contents to the under, with some minor changes.
[Match]
Name=interface
[Network]
DHCP=sure
DNS=server1
DNS=server2
Domains=~.
[DHCPv4]
UseDNS=no
[DHCPv6]
UseDNS=no
Replace “interface” with the title you were given from ip hyperlink, and “server1” and “server2” with no matter DNS server IP addresses you need. You should claim one server, however you’ll be able to have 3 at maximum.
There are a few pieces I need to make clear.
One, enabling “DHCP” is essential. DHCP is enabled via default in case you don’t have a “.network” report for an interface. But whenever you create this report, it’s disabled until you permit it. This is essential as a result of an AP makes use of DHCP to offer your pc an IP cope with on its community. Without it, your pc is functionally invisible.
Two, disabling “UseDNS” is similarly essential. This is the toggle that determines whether or not your pc accepts the DNS servers the AP provides it (“yes”) or no longer (“no”). Since our goal is to customise DNS, we want to inform the AP, “No thanks, I brought my own servers.”
The “DNS” and “Domains” pieces paintings as in systemd-resolved.
Once you save the report, reload systemd-networkd and systemd-resolved to reconfigure them. On my Linux Mint machine, I realized that systemd-networkd isn’t on via default. You can test if it’s enabled via working systemctl standing systemd-networkd. If you in finding it’s disabled, run those instructions with superuser privileges.
systemctl permit systemd-networkd
systemctl get started systemd-networkd
systemctl restart systemd-resolved
Otherwise, run those (additionally as superuser).
systemctl restart systemd-networkd
systemctl restart systemd-resolved
The procedure for verifying your settings is equal to converting systemd-resolved’s world settings, so practice the ones steps in my earlier article.
Querying for Answers within the Wrong Places
My largest motivation for writing those articles, greater than educating DNS configuration, used to be as an example the significance of vetting data and doing issues the appropriate approach. There’s a large number of unhealthy recommendation at the matter of Linux DNS customization. Here are some examples I encountered.
Overwrite /and so forth/resolv.conf after which make the report immutable the use of Linux report permissions. Brute drive strategies like this are by no means smart. Because systemd-resolved remains to be working, you make your machine waste sources futilely writing to an immutable report. This would possibly no longer paintings, both, as a result of many Linux distros go queries to systemd-resolved by the use of the D-Bus, no longer via querying the stub listener uncooked by the use of /and so forth/resolv.conf.
Disable systemd-resolved to make /and so forth/resolv.conf a static report once more, then write your adjustments into it. As a lot as I’d love to restore the previous tactics, systemd is simply too embedded to return. Moreover, essential machine elements depend on systemd-resolved, so in case you flip it off, they may ruin.
Install dnsmasq for DNS caching. This makes no sense as a result of systemd-resolved already caches DNS responses. Why soak up the disk house and replica the sources? I will be able to perceive an peculiar Linux person no longer understanding this, however can one dispense this recommendation with out understanding it’s redundant?
Closing Address
With this workout in the back of me, I took away two courses value underscoring.
First, in case you search solutions on-line, test them towards the guide. Even when learning the resources I cited, that have been assessed to be credible, I nonetheless checked them towards the guide. The guy pages are flooring fact and are available preinstalled, so why wouldn’t you seek the advice of them?
Second, the one strategy to in point of fact validate your paintings is to learn the logs. I’ve my gripes with systemd, however something it does smartly is logging. Because other systemd elements are performed as other machine customers, you’ll be able to run journalctl and specify the person whose logs you need.
Hopefully, I’ve carried out my task, and I’m no longer the one person who realized one thing from this.
Suggest a Topic
Is there an educational you’d like to peer featured?
Email your concepts to me, and I’ll believe them for a long run column.
And use the Reader Comments function under to supply your enter!






No Comment! Be the first one.