A brand new record from cloud safety corporate ZScaler sheds gentle at the rising cellular threats on Android running methods, in addition to IoT and OT gadgets threats. The findings come as greater than 60% of the worldwide Internet visitors is now generated by way of cellular gadgets and financially-oriented cellular threats have grown by way of 111% during the last yr.
An inventory of cellular malware threats
ZScaler’s ThreatLabz witnessed a 29% upward thrust in banking cellular malware over the former yr, with banking malware representing 20% of the overall Android danger panorama.
Most lively banking malware households up to now come with:
- Vultur, which is essentially disbursed in the course of the Google Play Store.
- Hydra, disbursed by the use of phishing messages, web pages, and malicious Google Play Store packages.
- Ermac, designed to scouse borrow monetary knowledge from banking and pockets apps.
- Anatsa, sometimes called TeaBot
- Coper, sometimes called Octo
- Nexus, essentially objectives cryptocurrency accounts
Most of those banking malware document keystrokes, hijack credentials, and intercept SMS messages in an effort to bypass Multi-Factor Authentication.
SEE: How to Create an Effective Cybersecurity Awareness Program (roosho Premium)
Spyware threats jump by way of greater than 100%
In addition to banking malware, spyware and adware threats have additionally grown, with researchers indicating that blocked transactions larger by way of 100% over the former yr.
The maximum prevalent spyware and adware reported are SpyLoan, SpinOk, and SpyNote.
- SpyLoan has the power to scouse borrow non-public knowledge from gadgets, equivalent to accounts, tool data, name logs, put in apps, calendar occasions, metadata, and extra.
- SpinOk spyware and adware collects delicate knowledge and information from quite a lot of places at the inflamed tool and exfiltrates the information to an attacker-controlled server.
- SpyNote, sometimes called CypherRat, supplies further far flung get entry to functions in order that the attacker can keep an eye on execution of device at the cellular tool.
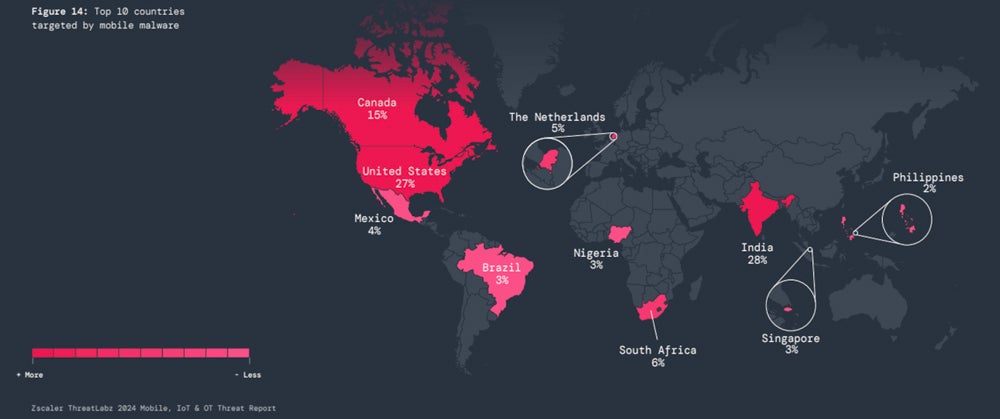
According to ZScaler, maximum cellular malware focused India (28%), the U.S. (27%), and Canada (15%), adopted by way of South Africa (6%), The Netherlands (5%), Mexico (4%), Nigeria (3%), Brazil (3%), Singapore (3%) and the Philippines (2%).
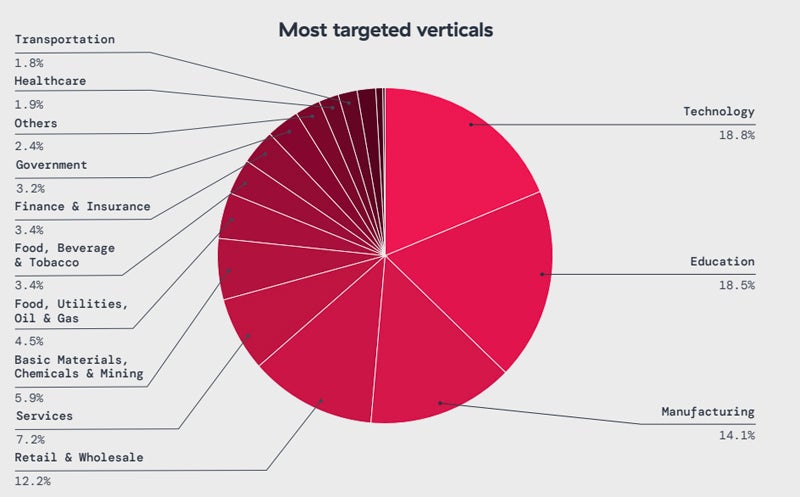
Impacted sectors come with era (18%), schooling (18%), production (14%), retail and wholesale (12%), and services and products (7%).
Mobile malware are disbursed by the use of quite a lot of strategies. One manner is composed of the use of social engineering tactics. As an instance, ZScaler reviews that attackers deployed the Copybara cellular malware by way of the use of voice phishing (vishing) assaults, the place the sufferer gained voice directions to put in the malware on their Android telephones.
QR code rip-off may be not unusual, the place sufferers are tricked into scanning malicious QR codes resulting in malware infections or, in some circumstances, to phishing pages.
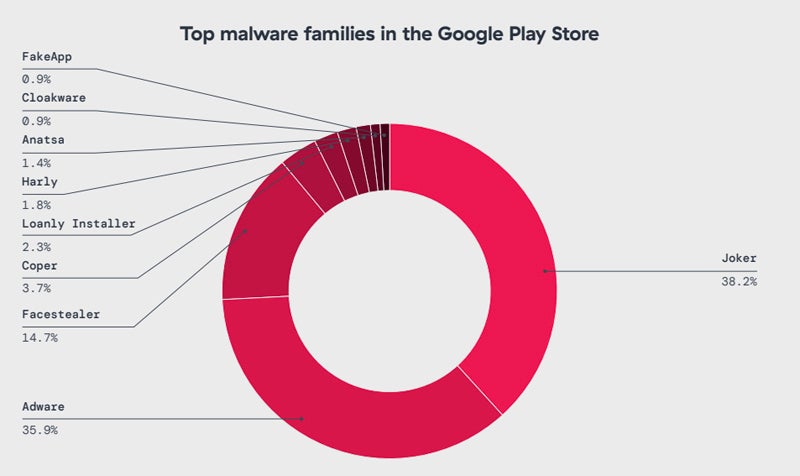
Some malware may be to be had at the Google Play Store. This comprises Joker — which silently subscribes customers to top rate services and products with out their consent to generate fees — adopted by way of spy ware malware sort and facestealer, a Facebook account stealer.
Overall, regardless of an general lower in Android assaults, financially-oriented cellular threats have grown by way of 111% during the last yr.
IoT and OT threats
Internet of Things and Operational Technology environments stay increasing and are more and more focused by way of attackers, in step with the record. The researchers point out that the collection of IoT gadgets interacting with them has grown by way of 37% year-over-year.
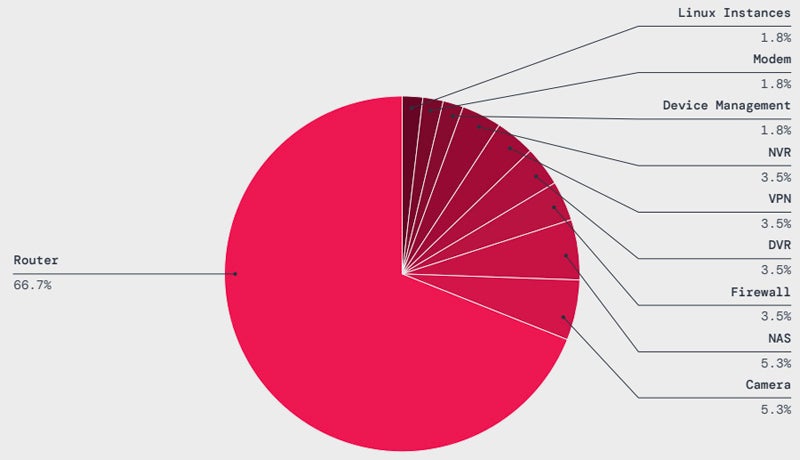
IoT malware assaults have grown by way of 45% over the last yr, with routers being probably the most focused form of tool, with greater than 66% of assaults aimed toward those gadgets. The main malware households hitting IoT gadgets are Mirai (36.3%) and Gafgyt (21.2%). Botnets constructed with those malware on IoT gadgets can be utilized to release vast Distributed Denial of Service assaults.
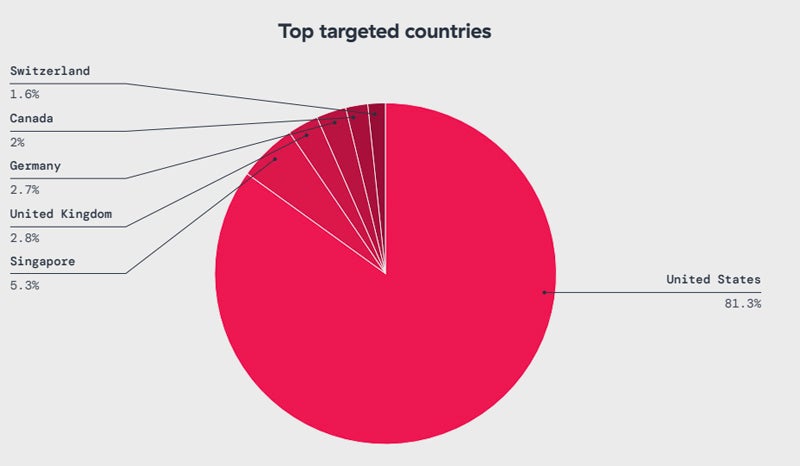
Regarding the geographical distribution, greater than 81% of IoT malware assaults are aimed on the U.S., adopted by way of Singapore (5.3%), the United Kingdom (2.8%), Germany (2.7%), Canada (2%), and Switzerland (1.6%).
Top sectors impacted by way of IoT malware assaults are production (36.9%), transportation (14.2%), meals, beverage, and tobacco (11.1%).
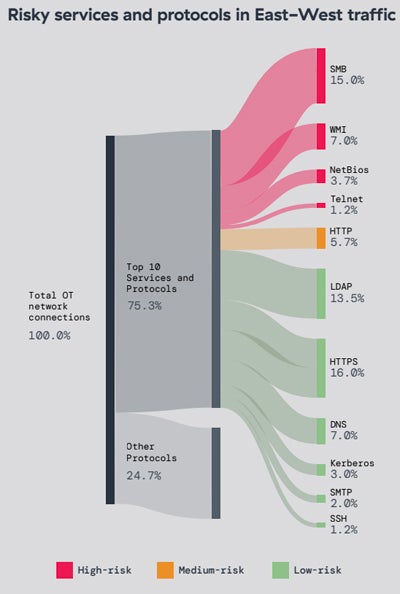
On the OT aspect, 50% of the gadgets in lots of deployments use legacy, end-of-life running methods. Protocols at risk of other vulnerabilities also are continuously uncovered in OT environments, equivalent to SMB or WMI.
As an instance, ThreatLabz analyzed the OT content material of a large-scale production group, comprising greater than 17,000 attached OT gadgets throughout greater than 40 other places. Each website contained greater than 500 OT gadgets with end-of-life Microsoft Windows running methods, a lot of which had recognized vulnerabilities.
67% of the worldwide visitors to the OT gadgets used to be unauthorized or blocked.
What will the long run appear to be?
According to ZScaler, IoT and OT gadgets will stay number one danger vectors, whilst the producing sector will stay a most sensible goal for IoT assaults, together with ransomware.
ZScaler additionally suspects synthetic intelligence will probably be more and more used to ship fine quality phishing campaigns focused on cellular customers. However, AI may even assist defenders automate vital purposes and higher prioritize their efforts.
How to offer protection to IoT and OT gadgets from cyber assaults
To give protection to from threats on IoT and OT gadgets, it can be crucial to:
- Gain visibility on IoT and OT gadgets is a concern. Organizations want to uncover, classify, and take care of lists of all IoT and OT gadgets used of their complete setting.
- Keep all methods and device up-to-the-minute and patched to forestall being compromised by way of not unusual vulnerabilities.
- Network logs will have to be amassed and analyzed. Suspicious consumer account get entry to and device occasions will have to be specifically monitored.
- Multi-factor authentication will have to be deployed when conceivable, and default passwords and accounts will have to be modified or disabled.
- Zero-Trust tool segmentation must be enforced for IoT and OT property to reduce knowledge publicity.
How to offer protection to cellular gadgets from cyber assaults
To give protection to from threats on cellular gadgets, it is very important:
- Install safety packages at the gadgets, to offer protection to them from malware and conceivable phishing makes an attempt.
- Any hyperlink arriving at the cell phone, regardless of the applying, must be cautiously tested. In case of suspicious hyperlink, it will have to now not be clicked and reported to IT safety body of workers.
- Unknown packages will have to be have shyed away from. Also, packages must by no means be downloaded from 3rd events or untrusted resources.
Companies must even be wary of packages soliciting for updates instantly after set up. An utility downloaded from the Play Store must be the newest model. If an app requests permission to replace instantly after set up, it must be handled as suspicious and may point out malware making an attempt to obtain further malicious parts.
Disclosure: I paintings for Trend Micro, however the perspectives expressed on this article are mine.






No Comment! Be the first one.