Group-IB researchers report a pointy rise in Eldorado – Golang-based ransomware with cross-platform encryption- operations, concentrating on varied industries. Learn how Eldorado ransomware associates function and the right way to shield your enterprise from assaults.
Group-IB Threat Intelligence analysts have reported an increase in assaults involving Eldorado, a Go-based ransomware, promoted by its operators on RAMP ransomware boards to search out expert associates. The new assault must be regarding for customers, particularly these on Linux, because of the rising ransomware threats in opposition to Linux servers.
RAMP is reportedly, some of the fashionable boards for ransomware gangs, selling 60% of latest RaaS (ransomware-as-a-service) applications between 2022 and 2023.
During this era, Group-IB recognized 27 RaaS program adverts on darkish internet boards, together with well-known applications like Yanluowang, Qilin, Knight, and qBit and in addition lesser-known instruments. In 2023, the variety of adverts looking for companions for RaaS applications elevated by 1.5 occasions, indicating a rising demand for expert associates. In March 2024, researchers got here throughout a ransomware associates program for Eldorado on RAMP, began by a consumer going by “$$$” selling a locker and loader for pentesters.
Eldorado is a cross-platform ransomware written in Golang. It makes use of the Chacha20 algorithm for file encryption and RSA-OAEP (Rivest Shamir Adleman-Optimal Asymmetric Encryption Padding) to encrypt generated keys on Windows and Linux platforms. It comes with a consumer handbook for 32/64-bit variants for VMware ESXi hypervisors and Windows, making it tough to get well recordsdata with out the decryption key.
Eldorado associates additionally use SMB (Server Message Block) protocol to encrypt massive recordsdata on a sufferer’s community, utilizing instruments like lockers, loaders, encryptors, and ransom notes. SMB permits pc sharing of recordsdata and printers over a community. The ransom observe additionally features a URL for a dwell chat with attackers to barter a ransom worth.
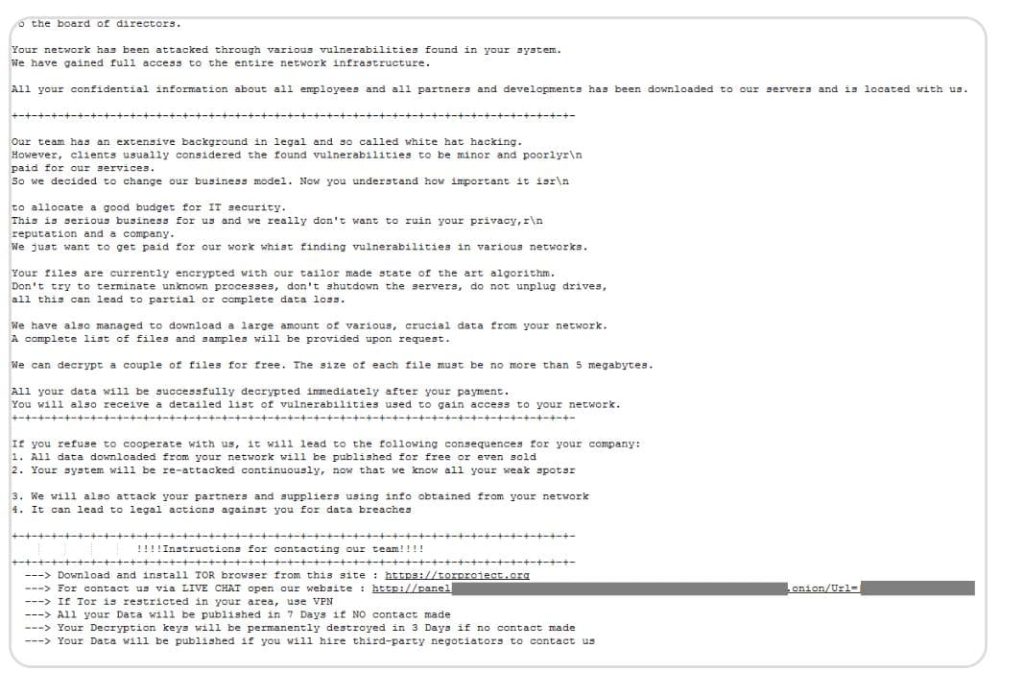
“The Eldorado group has managed to develop and deploy a highly effective ransomware builder, which has been used to target both Windows and Linux systems,” researchers wrote in a weblog put up.
For your data, this group runs a RaaS enterprise offering associates with the instruments and assist wanted to hold out ransomware assaults. Affiliates can goal each Windows and Linux methods. Researchers imagine them to be Russian as their posts on the boards are in Russian and a few include expressions used solely by “native Russian speakers.”
Until June 2024, 16 firms throughout completely different international locations and industries had been focused by Eldorado ransomware assaults, with the US being probably the most affected. The most focused business was Real Estate (3 assaults) accounting for 18.75% of the entire assaults.
Other industries affected had been Education, Professional Services, Health Care, Manufacturing, Messaging and Telecommunications, Business Services, Administrative Services, Transportation, and Government and Military.
To shield in opposition to Eldorado ransomware assaults, companies ought to implement multi-factor authentication and credential-based entry options, and usually again up information to keep away from paying the ransom.
Jason Soroko, Senior Vice President of Product at Sectigo commented on the newest growth stating “Eldorado’s evasiveness is enhanced by ‘living off the land’, which means that it makes use of instruments which might be already accessible on contaminated methods. Windows WMI and PowerShell are examples. These instruments can be utilized to maneuver laterally or encrypt assets.“
“Interestingly, Eldorado can be configured in Windows to not affect certain kinds of files that are critical for normal operation such as DLLs,” Jason defined. “The Windows variant of this malware seems to be highly configurable, which is why we see different variations on the method of attack from the same malware.”
“Eldorado ransomware also exhibits advanced capabilities for lateral movement, notably through USB drive checks. This feature allows it to detect and infect removable media, facilitating the spread of the ransomware to other systems when the infected USB drive is connected elsewhere,” Jason warned. “The malware scans for connected USB drives and automatically copies itself onto them, often using obfuscation techniques to avoid detection by security software.”
- New Cylance Ransomware Targets Linux and Windows
- Volcano Demon Ransomware Makes Phone Calls for Ransom
- New AcidRain Linux Malware Variant “AcidPour” Targeting Ukraine
- No More Ransom Offers Free LockerGoga Ransomware Decryptor
- Universal decryptor key for Sodinokibi, REvil ransomware launched






No Comment! Be the first one.