A brand new phishing marketing campaign makes use of faux CAPTCHA verification pages to trick Windows customers into operating malicious PowerShell instructions, putting in the Lumma Stealer malware and stealing delicate info. Stay knowledgeable and guarded.
Cybersecurity researchers at CloudSec have found a brand new phishing marketing campaign that’s tricking customers into operating malicious instructions by faux human verification pages. The marketing campaign, which primarily targets Windows customers, goals to put in the Lumma Stealer malware, resulting in the theft of delicate info.
How the Attack Works
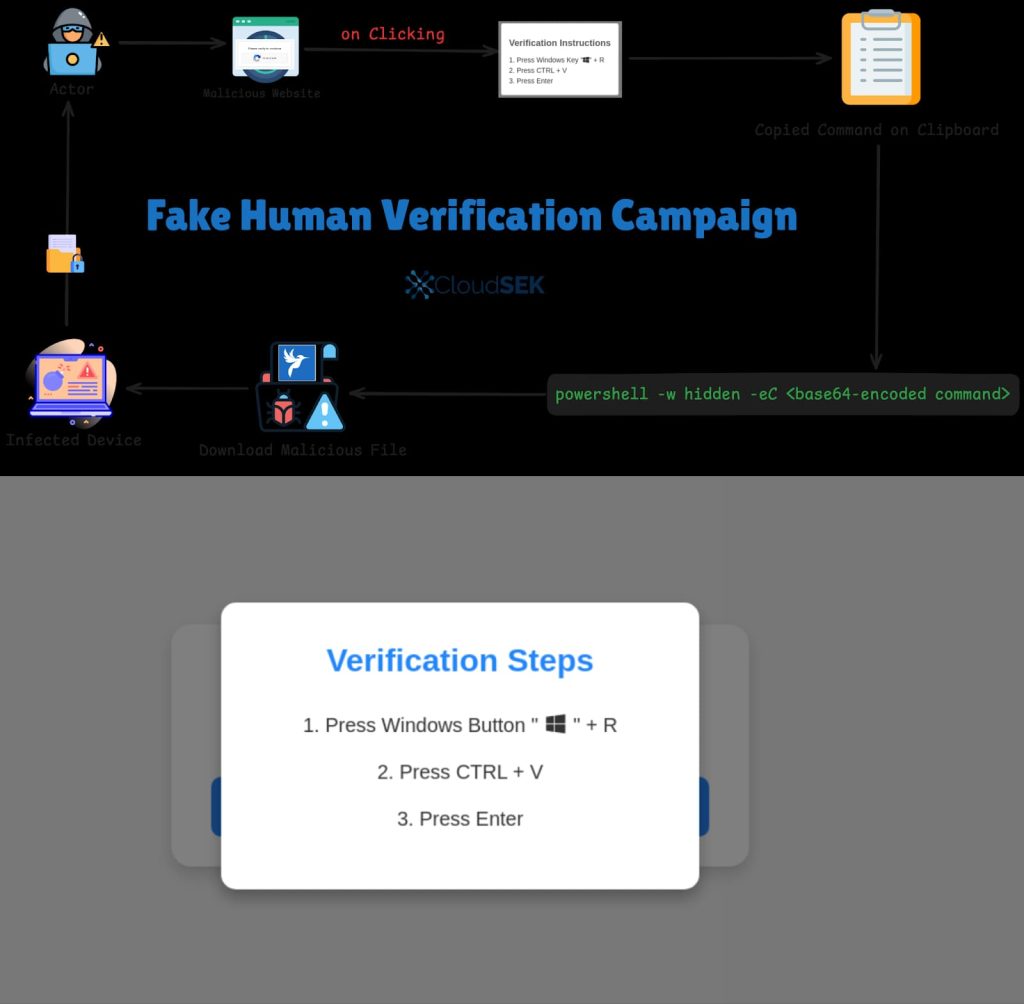
Threat actors are creating phishing websites hosted on numerous platforms, together with Amazon S3 buckets and Content Delivery Networks (CDNs). These websites mimic reputable verification pages, resembling faux Google CAPTCHA pages. When customers click on the “Verify” button, they’re introduced with uncommon directions:
- Open the Run dialog (Win+R)
- Press Ctrl+V
- Hit Enter
Unknown to the consumer, these actions execute a hidden JavaScript perform that copies a base64-encoded PowerShell command to the clipboard. When the consumer pastes and runs the command, it downloads the Lumma Stealer malware from a distant server.
CloudSec’s report shared with Hackread.com forward of publishing on Thursday, revealed that the downloaded malware usually downloads extra malicious elements, making detection and removing tougher. While at the moment used to unfold Lumma Stealer, this system might be simply tailored to ship different kinds of malware.
For your info, the Lumma Stealer is designed to steal delicate information from the contaminated gadget. While the particular information focused can differ, it usually consists of login credentials, monetary info, and private information. This newest marketing campaign got here simply days after the malware was caught disguising itself as an OnlyFans hacker software, infecting the units of different hackers.
In January 2024, Lumma was found to be spreading by cracked software program distributed through compromised YouTube channels. Earlier, in November 2023, researchers had recognized a brand new model of LummaC2, known as LummaC2 v4.0, which was stealing consumer information utilizing trigonometric strategies to detect human customers.
I hereby affirm. https://t.co/1q4cARQLDM pic.twitter.com/GEBzqJeaSs
— Waqas (@WAK4S) December 31, 2023
What Now?
Now that the brand new Lumma stealer an infection spree has been reported, companies and unsuspecting customers want to remain alert and keep away from falling for the newest faux verification rip-off. Here are some commonsense guidelines and easy but important suggestions for defense in opposition to Lumma and different related stealers:
- Educate your self and others: Share this info with mates, household, and colleagues to boost consciousness about this new menace.
- Be cautious of bizarre verification requests: Legitimate web sites not often ask customers to execute instructions by the “Run” dialogue field. Be suspicious of any web site that makes such requests.
- Don’t copy and paste unknown instructions: Avoid copying and pasting something from untrusted sources, particularly instructions meant to be run in a terminal or command immediate.
- Keep your software program up to date: Ensure your working system and antivirus software program are up-to-date to patch recognized vulnerabilities.
- Most Important: Follow Hackread.com for the newest cybersecurity information.
RELATED TOPICS






No Comment! Be the first one.