On the primary day of Cybersecurity Awareness Month within the U.S., analysis has published that the selection of important world cyber assaults in 2024 shall be double that of 2020.
A brand new document from insurer QBE, Connected Business: virtual dependency fuelling chance, predicts that organisations shall be hit by way of 211 disruptive and damaging cyber assaults this yr.
Disruptive incidents are reversible and most effective affect information availability, integrity, or get admission to — akin to allotted denial-of-service assaults. Conversely, damaging assaults are irreversible and goal to have a bodily affect on other people, just like the Triton malware, which disabled protection techniques at petrochemical crops.
The selection of disruptive and damaging cyber assaults in 2020 was once 103, indicating a possible 105% build up in simply 4 years.
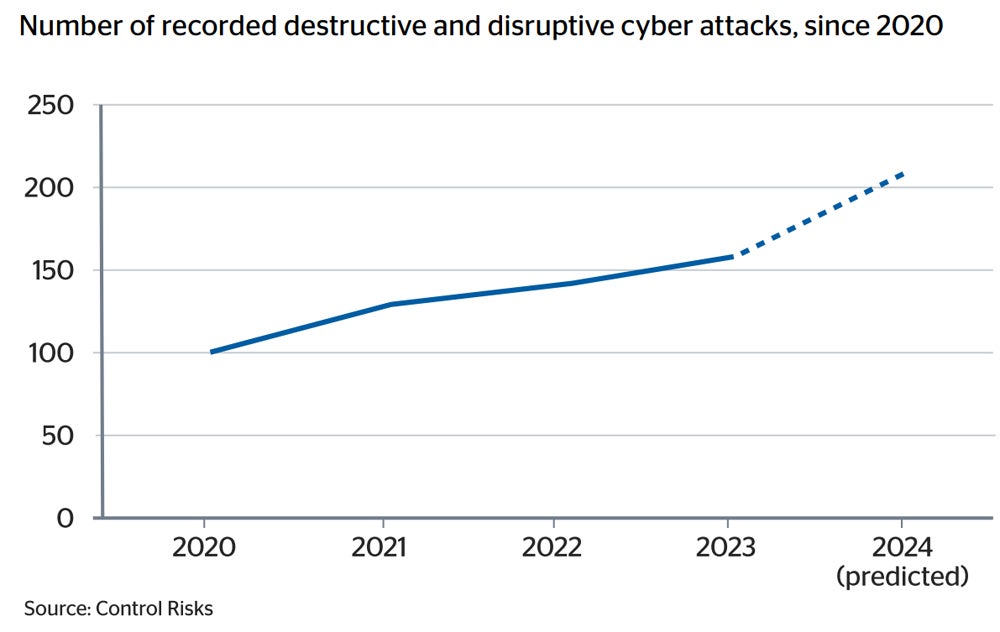
The information for the document was once accrued by way of the consultancy Control Risks. They listed a collection of “strategically important” open-source and incident reaction instances fairly than information loss or easy tool compromise kind incidents.
Examples of those important assaults from the final 4 years come with the:
SEE: Ransomware Cheat Sheet: Everything You Need To Know In 2024
However, QBE instructed roosho that the actual figures for disruptive and damaging assaults are most likely a ways upper than what’s reported.
“As technology interdependencies grow, we expect more cyber incidents to disrupt many companies in a single attack, meaning businesses are more likely to experience a disruptive cyber event,” the authors wrote.
“Malicious actors can also target specific companies to cause greater damage, whether they’re extorting ransoms or destabilising geopolitical rivals.”
Ransomware attackers goal operational tech and massive firms for larger paydays
The document unearths that operational generation operators and massive organisations are high objectives for ransomware attackers.
As neatly as having strict uptime necessities, OT organisations managing important infrastructure are identified for depending on legacy gadgets, as changing generation whilst keeping up customary operations is each difficult and dear.
Evidence from NCC Group submitted for a U.Okay. executive document on the specter of ransomware to nationwide safety discovered that “OT systems are much more likely to include components that are 20 to 30 years old and/or use older software that is less secure and no longer supported.”
This makes OT firms each out there and prone to pay a ransom, as downtime could have serious penalties. Indeed, the QBE document claimed that ransomware assaults towards business sector organisations surged by way of 50% from 2022 to 2023.
Another crew prone to envisage to an attacker’s calls for are the executives of huge firms, as they view operational disruption as extra pricey. According to QBE, a median of 61% of organisations with annual revenues of $5 billion payout ransoms after an assault, in comparison with 25% of the ones with annual revenues beneath $10 million.
These ways have confirmed profitable. The moderate ransomware payout of 2023 was once $2 million, a five-fold build up over 2022. The document’s authors say that a hit regulation enforcement operations — as an example, the LockBit, BlackCat, and Hive takedowns — have led attackers to hone in on wealthier objectives so they are able to maximise ransom bills sooner than they stopped.
Furthermore, now that takedowns are changing into extra widespread, professionals say that ransomware teams might view executive retaliation as “inevitable,” and due to this fact haven’t any reservations about concentrated on broad or important organisations.
Researchers at the back of the QBE document are expecting that the selection of ransomware sufferers will upward push by way of 11% from 2023 to 2025, with production, healthcare, IT, schooling, and executive sectors maximum in peril.
Another ransomware methodology the document highlights that attackers use for optimum affect is concentrated on IT provide chains. One reason why is because of the selection of firms reliant on their services and products making uptime extra important, as with CNI. But the opposite is as a result of they devise the chance to hit many organisations throughout sectors thru a unmarried assault.
Over three-quarters of third-party incidents in 2023 are because of simply 3 provide chain vulnerabilities, the document unearths.
Artificial intelligence as a supply of each worry and hope for U.Okay. undertaking safety
As neatly as the brand new document, QBE additionally surveyed 311 IT resolution makers within the U.Okay. in September about their safety considerations, with AI, after all, being the freshest subjects.
It published {that a} small, however important, 15% portion idea AI would carry the danger of cyber assault. This is essential, as 69% of medium-to-large U.Okay. companies stated that they had already confronted disruption from cyber occasions prior to now yr.
In June, HP intercepted an e mail marketing campaign spreading malware with a script that “was highly likely to have been written with the help of GenAI.” AI can decrease the barrier to access for cyber crimes, as less-skilled criminals can use it to generate deepfakes, to scan networks for access issues, for reconnaissance, and extra.
At the beginning of the yr, a finance employee in Hong Kong paid out $25 million to hackers that used AI to impersonate the manager monetary officer. They mimicked the executives voice all through telephone calls to authorise the switch.
SEE: Report Reveals the Impact of AI on Cyber Security Landscape
On the opposite hand, 32% of U.Okay. companies instructed QBE that they really feel AI will make stronger their cyber coverage, and the Control Risks researchers stated it’s going to spice up the potency of safety and defensive actions.
David Warr, the QBE Insurance Portfolio Manager for Cyber, stated: “AI is each a hindrance and a assist to the cyber panorama. As AI turns into extra extensively out there, cybercriminals and cyber activists can release larger-scale assaults at a sooner tempo. This larger capacity in scale and pace attributable to AI may threaten the cyber area. However, managed and controlled use of AI too can assist locate cyber vulnerabilities.
“Companies in the U.K. and around the world both big and small should be building up their resilience to both mitigate against cyber threats and be prepared to act in the event of a cyber-attack.”






No Comment! Be the first one.