Let’s say you’ve written a bash script that scans your whole Linux servers in your information middle for uptime. Such a file may comprise the next contents:
ssh $1 "uptime"
Whenever you run your script, it might get foiled by a difficulty the place it’s stopped by a server that has but to have its SSH key fingerprint added to the known_hosts file. When this occurs, your script is rendered ineffective.
SEE: The best way to View Your SSH Keys in Linux, macOS, and Home windows (roosho)
SSH key fingerprint
What’s an SSH key fingerprint? Easy: The important thing’s fingerprint is verified while you attempt to log in to a distant laptop utilizing SSH. Whenever you log into an SSH server for the primary time, you’ll see one thing like that proven beneath.
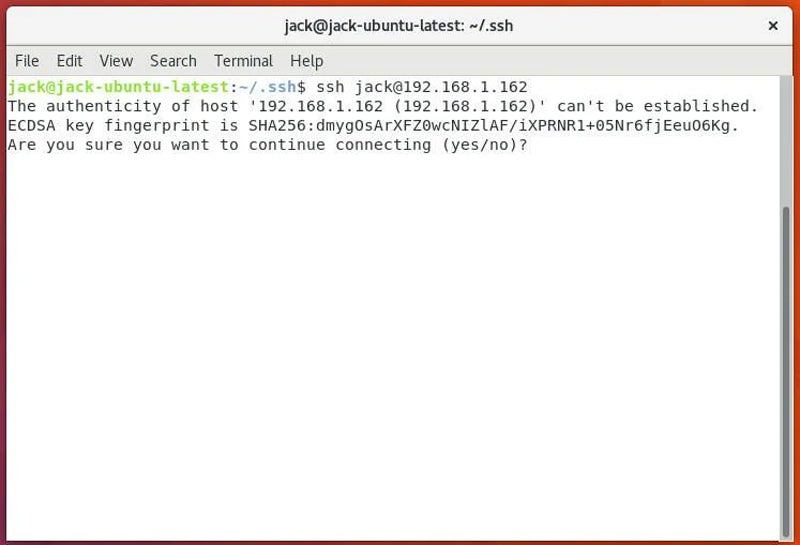
If you happen to don’t settle for the fingerprint, the connection will likely be instantly damaged. So what occurs while you’re working with a bash script that can’t settle for enter with the intention to okay the addition of the distant SSH fingerprint?
Thankfully, the builders of SSH considered this and added a command that lets you simply add SSH fingerprints to the known_hosts file.
SEE: The best way to Create and Copy SSH Keys with 2 Easy Instructions (roosho)
Including the fingerprint
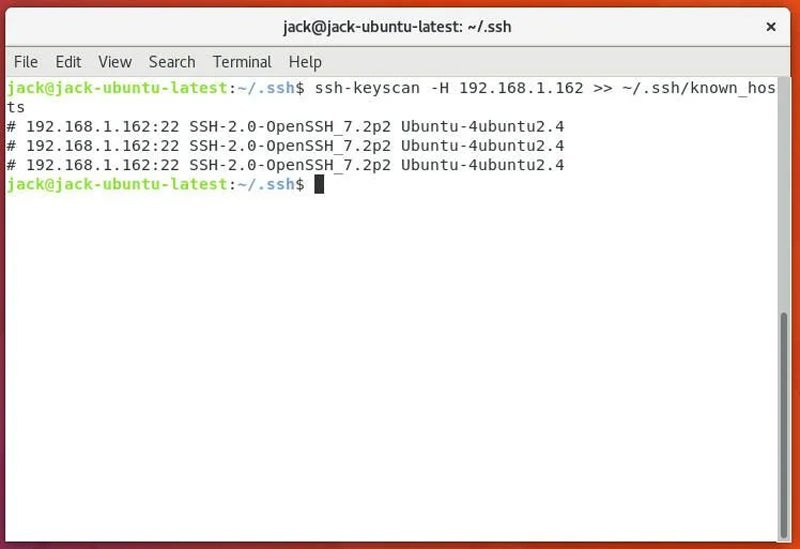
I’ll show including the fingerprint from a distant server to a neighborhood machine. Let’s say the distant server is at 192.168.1.162. So as to add that fingerprint, the command can be:
ssh-keyscan -H 192.168.1.162 >> ~/.ssh/known_hosts
The command will run and add the distant SSH fingerprint to the native machine with out your enter, as proven beneath.
So an addition to the bash script may appear to be:
ssh-keyscan $1 >> ~/.ssh/known_hosts
The above addition would take the argument from the command (say, for instance, ./script 192.168.1.118) and add the fingerprint to ~/.ssh/known_hosts earlier than it then strikes to the subsequent line — thereby avoiding the lacking SSH fingerprint concern. In fact the above would solely work correctly when you’ve got ssh key authentication setup. In any other case, you’d should enter the distant machine’s password.
SEE: The best way to Mount Distant Directories with SSH (roosho)
The easy issues
Typically, it’s the easy issues that journey up our bash scripts. If that key fingerprint concern has been inflicting you complications along with your scripts, now you can keep away from the problem.






No Comment! Be the first one.