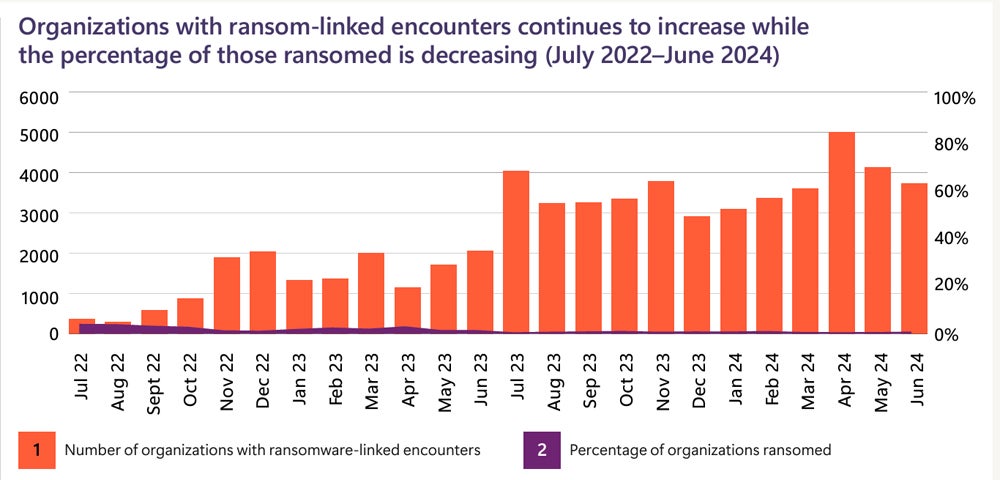
The selection of tried ransomware assaults on Microsoft consumers globally have grown dramatically within the ultimate yr, in line with Microsoft’s Digital Defense file, launched on Oct. 15. However, developments in computerized assault disruption applied sciences have resulted in fewer of those assaults attaining the encryption level.
Microsoft reported 600 million cybercriminal and countryside assaults going on day by day. While ransomware makes an attempt greater by means of 2.75 instances, a success assaults involving knowledge encryption and ransom calls for dropped by means of three-fold.
Significant assault sorts come with deepfakes, e-commerce robbery
Microsoft says it “tracks more than 1,500 unique threat groups — including more than 600 nation-state threat actor groups, 300 cybercrime groups, 200 influence operations groups, and hundreds of others.” The most sensible 5 ransomware households — Akira, Lockbit, Play, Blackcat, and Basta — accounted for 51% of documented assaults.
According to the file, attackers maximum continuously exploit social engineering, identification compromises, and vulnerabilities in public-facing programs or unpatched running methods. Once inside of, they continuously set up faraway tracking equipment or tamper with safety merchandise. Notably, 70% of a success assaults concerned faraway encryption, and 92% focused unmanaged gadgets.
Other primary forms of assaults incorporated:
- Infrastructure assaults.
- Cyber-enabled monetary fraud.
- Attacks on e-commerce areas, the place bank card transactions don’t require the cardboard to be bodily provide.
- Impersonation.
- Deepfakes.
- Account takeover.
- Identity and social engineering assaults — maximum (99%) of that have been password robbery assaults.
- SIM swapping.
- Help table social engineering, the place attackers impersonate consumers to reset passwords or attach new gadgets.
- Credential phishing, in particular via phishing-as-a-service tasks. Often those are brought on by means of HTML or PDF attachments containing malicious URLs.
- DDoS assaults, which brought about an international outage previous this yr.
Antivirus tampering was once additionally a significant participant within the earlier yr: Over 176,000 incidents Microsoft Defender XDR detected in 2024 concerned tampering with safety settings.
SEE: Ransomware actors can goal backup knowledge to take a look at to drive a fee.
Nation-state, financially motivated actors proportion ways
Both financially-motivated risk actors and countryside actors more and more use the similar knowledge stealers and command-and-control frameworks, Microsoft discovered. Interestingly, financially-motivated actors now release cloud identification compromise assaults — a tactic prior to now related to countryside attackers.
“This year, state-affiliated threat actors increasingly used criminal tools and tactics — and even criminals themselves — to advance their interests, blurring the lines between nation-state backed malign activity and cybercriminal activity,” the file said.
Microsoft tracks primary risk actor teams from Russia, China, Iran, and North Korea. These geographical regions might both leverage monetary risk actors for benefit or flip a blind eye to their actions inside of their borders.
According to Tom Burt, Microsoft’s company vice chairman of purchaser safety and consider, the ransomware factor highlights the relationship between countryside actions and financially motivated cybercrime. This drawback is exacerbated by means of nations that both exploit those operations for benefit or fail to do so towards cybercrime inside of their borders.
Expert Evan Dornbush, former NSA cybersecurity knowledgeable, gives views at the topic:
“This report signals one trend currently getting little attention and likely to define the future of cyber: the amount of money criminals can earn,” he mentioned in an e mail to roosho. “Per the Microsoft report, government, as a sector, only makes up 12% of the aggressors’ targeting sets. The vast majority of victims are in the private sector.”
The sectors maximum focused by means of countryside risk actors this yr had been:
- IT.
- Education .
- Government.
- Think tanks and NGOs.
- Transportation.
Both attackers and defenders use generative AI
Generative AI introduces a brand new set of questions. Microsoft recommends proscribing generative AI’s get entry to to delicate knowledge and making sure that knowledge governance insurance policies are carried out to its use. The file outlines AI’s important affects on cybersecurity:
- Both attackers and defenders more and more use AI equipment.
- Nation-state actors can generate misleading audio and video with AI.
- AI spear phishing, résumé swarming, and deepfakes are actually not unusual.
- Conventional strategies of proscribing overseas affect operations might not paintings.
- AI insurance policies and ideas can mitigate some threat related to the usage of AI equipment.
- Although many governments agree on a necessity for safety as a very powerful aspect within the construction of AI, other governments pursue it in several tactics.
“The sheer volume of attacks must be reduced through effective deterrence,” Burt defined, “and while the industry must do more to deny the efforts of attackers via better cybersecurity, this needs to be paired with government action to impose consequences that further discourage the most harmful cyberattacks.”
How organizations can save you not unusual cyberattacks
The Microsoft file comprises movements organizations can take to forestall explicit forms of assaults. roosho distilled some actionable insights that follow around the board:
- Disrupt assaults on the method layer, because of this imposing insurance policies similar to for multi-factor authentication and assault floor relief.
- Similarly, use “secure-by-default” settings, which make multi-factor authentication obligatory.
- Use sturdy password coverage.
- Test pre-configured safety settings, similar to safety defaults or controlled Conditional Access insurance policies, in report-only mode to know their doable affect earlier than going reside.
- Classify and label delicate knowledge, and feature DLP, knowledge lifecycle, and Conditional Access insurance policies round high-risk knowledge and high-risk customers.
Microsoft put its Secure Future Initiative in position this yr, after the Chinese intrusion into Microsoft executive e mail accounts in July 2023.






No Comment! Be the first one.