There are extra vulnerabilities round than ever. The Verizon Data Breach Investigations Report highlighted a virtually 200% expansion within the exploitation of vulnerabilities in 2023. In the primary seven months of 2024, new vulnerabilities rose by way of every other 30% in comparison to the former yr. No surprise vulnerability control gear are changing into a staple of the endeavor cybersecurity arsenal.
“Vulnerability management is a core function of cybersecurity,” mentioned Michelle Abraham, analysis director, Security and Trust at IDC. “Leaving vulnerabilities without action exposes organizations to endless risk since vulnerabilities may leave the news but not the minds of attackers.”
Top vulnerability control gear comparability
Many vulnerability control gear have equivalent options. But once I seemed into them extra carefully, I realized that they each and every have their very own center of attention or manner. Some are extra specialised than others. I in comparison them according to worth in addition to 4 key options:
- Cloud, on-prem, or each.
- Being a part of a complete cybersecurity suite.
- Automated discovery.
- Automated remediation.
Be conscious, then again, that an apples-to-apples comparability according to worth is unattainable because of the alternative ways distributors worth their services in addition to a loss of transparency on pricing.
| Starting worth | Cloud or on-prem | Cybersecurity suite options | Automated discovery | Automated remediation | |
|---|---|---|---|---|---|
| Tenable | About $4,000 consistent with yr for 100 property. | Cloud-based. There is a separate on-prem suite known as Tenable Security Center that comes with vulnerability control. | Vulnerability control, internet utility scanning, cloud safety, id publicity, operational era safety, connect floor control, and threat evaluation. | Yes | Yes |
| ESET | $275 for 5 units consistent with yr for the ESET Protect package deal that comes with ESET Vulnerability and Patch Management | Cloud-based. A separate on-prem suite is to be had that comes with vulnerability control | EDR, server safety, cellular danger protection, encryption, danger protection, cloud coverage, vulnerability & patch control, MFA, and MDR | Some automatic discovery however now not as wide as one of the others | Some auto-remediation functions are integrated |
| Syxsense | $9 consistent with software monthly or $960 consistent with yr for 10 units | One model for the cloud and every other for on prem | Patch control, vulnerability scanning, IT control, cellular software control, and nil believe | Yes | Yes |
| CrowdStrike | $184 consistent with yr for the overall suite and about $40 consistent with yr for Exposure Management | Cloud-based | EDR, antivirus, danger looking/intelligence, publicity control, AI, danger looking, cloud safety, SIEM, information coverage, automation | Yes | Yes |
| Qualys | $295 consistent with yr for the small trade model and about $2000 for the endeavor model. | Cloud-based with an on-prem model to be had. | Asset control, vulnerability & configuration control, threat remediation, danger detection & reaction, EDR, cloud safety, and compliance. | Yes | Yes |
| Rapid7 | $6 monthly consistent with asset or $2 monthly consistent with asset for a 500-asset license. | Cloud and on-prem | AI engine, XDR, publicity control, and assault floor control. | Yes | Yes |
| Ivanti | $4 monthly consistent with consumer. | Cloud or on-prem | Discovery, IT automation, real-time perception, endpoint control, community and endpoint safety, provide chain, and repair and asset control. | Yes | Yes |
| StorageGuard | $200 monthly for as much as 50 methods. | Cloud | No | Yes | Limited |
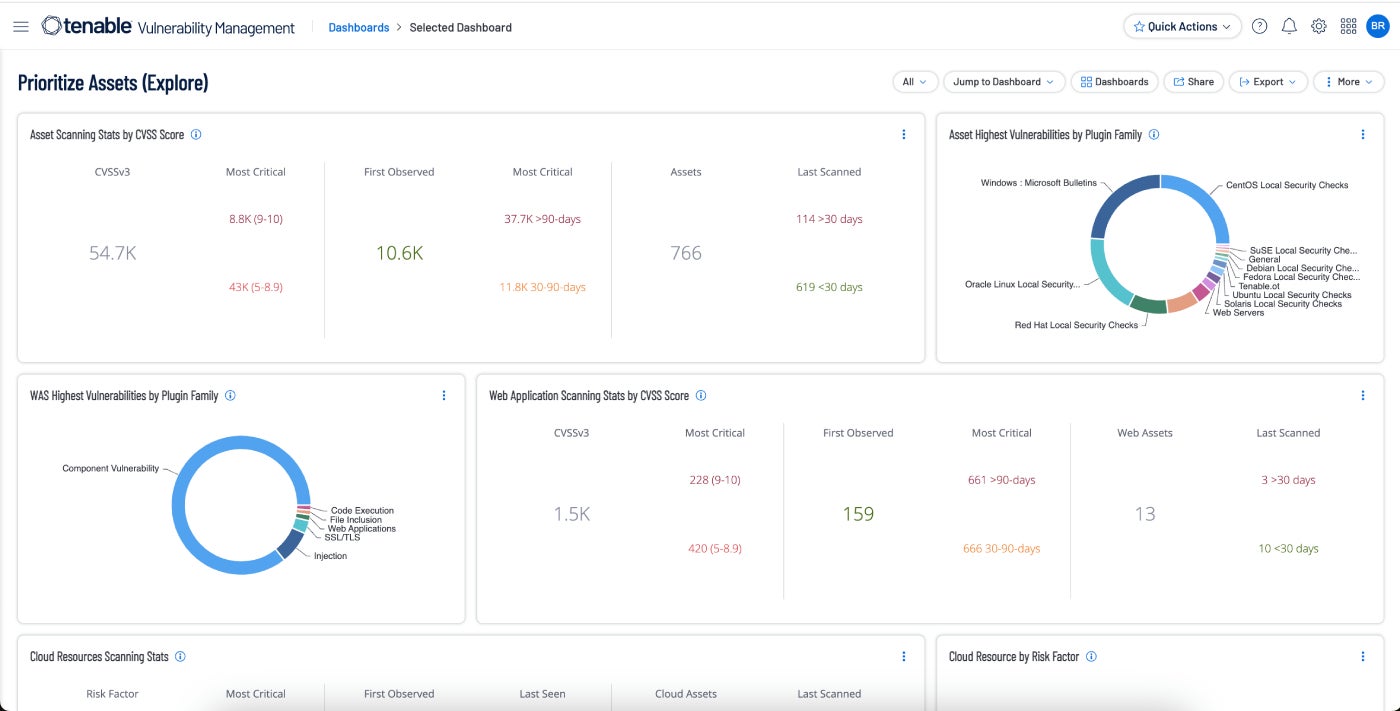
Tenable Vulnerability Management: Best general
Tenable Vulnerability Management takes a risk-based technique to vulnerability control. It specializes in community visibility with the intention to are expecting when assaults will happen and so that you could reply all of a sudden when crucial vulnerabilities are in play. A 60-day unfastened trial is to be had.
SEE: How to Create an Effective Cybersecurity Awareness Program (roosho Premium)
Why I selected Tenable
I decided on Tenable as the most productive general vulnerability control instrument general for plenty of causes. It is the marketplace chief amongst vulnerability control gear with a 25% marketplace percentage. It features a wealth of options and ticks as regards to the entire packing containers. It accommodates loads of integrations with different platforms and safety gear that make automation of workflows simple and cut back the selection of sources had to stay the endeavor secure.
Pricing
- Tenable prices about $4,000 consistent with yr for 100 property.
Features
- The Tenable Community is energetic with various customers keen to can help you cope with issues.
- Active and passive scanning of on-premise methods, digital machines, cloud cases, and cellular units.
- Cloud Connectors give steady visibility and evaluation into public cloud environments like Microsoft Azure, Google Cloud Platform, and Amazon Web Services.
- Built-in prioritization, danger intelligence, and real-time reporting lend a hand customers to grasp threat and proactively disrupt assault paths.
Pros and cons
| Pros | Cons |
|---|---|
| Fully built-in into the wider Tenable One platform. | Some customers record that make stronger may well be stepped forward. |
| Continuous, always-on discovery and evaluation | Real-time scanning and general scanning velocity may well be stepped forward. |
| Threat intelligence | Not the most affordable answer available on the market. |
| Automated vulnerability prioritization. | Better suited for skilled IT pros |
| Real-time visualization of threat, and monitoring of vulnerabilities, property, and remediations. | |
| Vulnerability threat ratings to spot threat. |
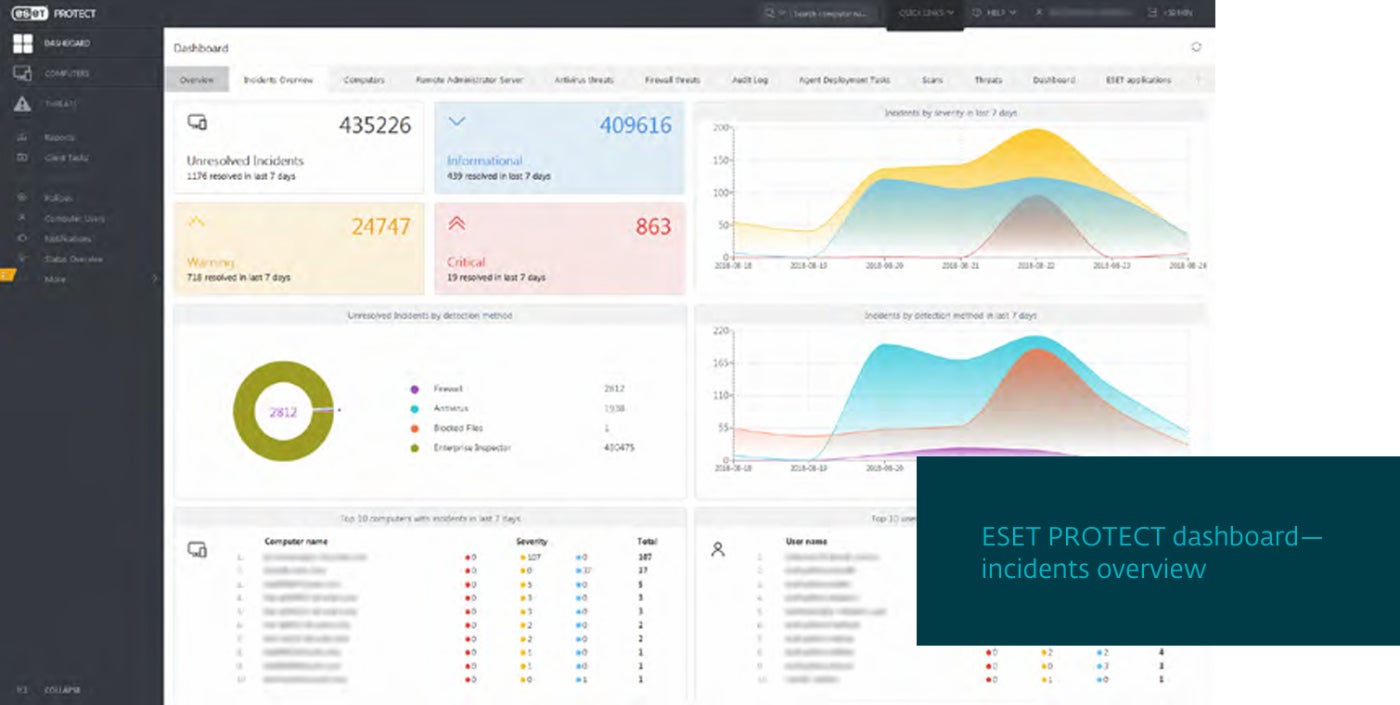
ESET Vulnerability and Patch Management: Best for SMEs
ESET Vulnerability and Patch Management can robotically scan hundreds of programs for any of tens of hundreds of commonplace vulnerabilities and exposures. It can prioritize and filter out vulnerabilities by way of publicity ranking and severity.
Why I selected ESET Vulnerability and Patch Management
I appreciated ESET as it’s simple to put in and run. This makes it horny for SMEs and bigger organizations that lack IT and cybersecurity sources.
Pricing
- $275 for 5 units consistent with yr for the ESET Protect package deal that comes with ESET Vulnerability and Patch Management.
Features
- Supports a couple of variations of Windows, Linux, and macOS.
- Detects over 35,000 CVEs.
- Automated scans with customizable time table settings.
- Prioritizes and filters vulnerabilities by way of publicity ranking and severity.
Pros and cons
| Pros | Cons |
|---|---|
| Simplifies patching by way of prioritizing crucial property and scheduling the rest for off-peak occasions. | Automated discovery and remediation options lack the scope of a few different answers. |
| Protection towards ransomware and zero-day threats. | More concentrated on small and mid-size organizations relatively than the endeavor marketplace. |
| Easy to arrange, use, and care for. |
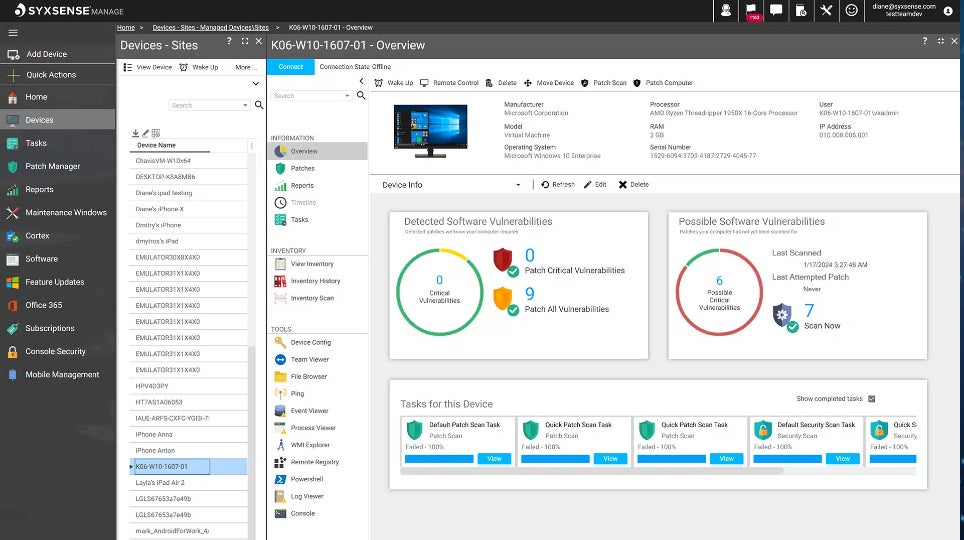
Syxsense Enterprise: Best for patch control
Syxsense Enterprise contains patch control, vulnerability scanning, IT control, and cellular software control inside of its vulnerability control platform. Most lately, it has added built-in remediation options in addition to 0 believe. Everything is now blended into one console by means of Syxsense Enterprise.
Why I selected Syxsense
Syxsense started lifestyles as a patch control specialist. Building on that luck, it has regularly expanded right into a complete featured vulnerability control suite. However, I realized that it doesn’t surround the breadth of safety modules that lots of the different distributors on this information. It is lacking SIEM, danger intelligence, and antivirus, for instance. Despite that, I appreciated the tight center of attention on vulnerability and software control. For those who have already got a safety platform and simply need to make stronger patch control and vulnerability control, Syxsense is a superb selection.
Pricing
- $9 consistent with software monthly or $960 consistent with yr for 10 units.
Features
- Automated discovery and remediation workflows.
- Comprehensive patch control together with patch supersedence, patch rollback, and patching any endpoint together with cellular units.
- A Zero Trust Evaluation Engine creates a depended on safety posture for endpoints.
Pros and cons
| Pros | Cons |
|---|---|
| Excellent patch control capability. | Syxsense was once simply bought by way of Absolute Security, which might hinder the top stage of continuing innovation that propelled Syxsense to the leading edge of the patch and vulnerability control box. |
| Tightly concentrated on vulnerability control. | Suite is lacking parts similar to antivirus, danger looking, and SIEM. |
| Separate variations for cloud and on-prem. |
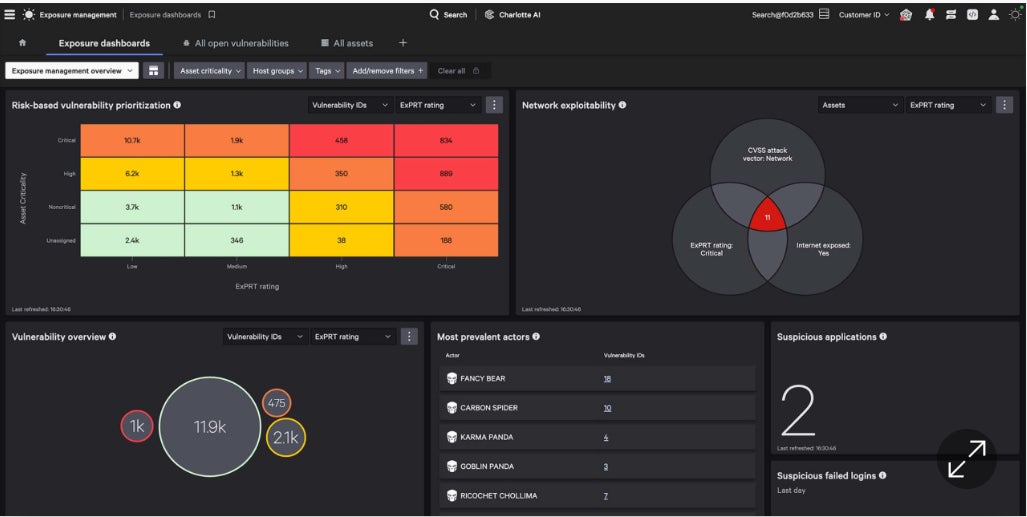
CrowdStrike Exposure Management: Best cybersecurity suite incorporating vulnerability control
CrowdStrike Exposure Management grew out of an older product referred to as Falcon Spotlight, which I used to be already accustomed to. I realized the way it broadens the functions of Falcon Spotlight by way of including extra of a threat control manner at the side of a number of AI-based functions.
Why I selected CrowdStrike Exposure Management
CrowdStrike Exposure Management is a cast product in its personal proper. It is one a part of a complete suite with a variety of safety features. Most patrons will acquire your entire CrowdStrike platform relatively than best the Exposure Management part. Known because the CrowdStrike Falcon Platform, it encompasses EDR, antivirus, danger looking/intelligence, publicity control, AI, danger looking, cloud safety, SIEM, information coverage, automation, and extra, all from a unmarried agent. Anyone wanting a vulnerability control instrument and a brand new safety suite can’t cross some distance mistaken adopting all the Falcon Platform.
Pricing
- $184 consistent with yr for the overall suite and about $40 consistent with yr for the publicity control module.
Features
- Automated evaluation for vulnerabilities, whether or not on or off the community.
- Shortened time-to-respond with real-time visibility into vulnerabilities and threats.
- The skill to prioritize and are expecting which vulnerabilities are perhaps to impact the group.
- The corporate boasts a unmarried lightweight-agent structure.
Pros and cons
| Pros | Cons |
|---|---|
| Vulnerability and patching orchestration. | Limited functions in terms of scanning for misconfigurations in safety programs. |
| Integration inside the CrowdStrike Falcon. | More center of attention on all the suite than on vulnerability control. |
| AI ties in combination danger intelligence with vulnerability evaluation in genuine time. | |
| A unmarried agent for all modules. |
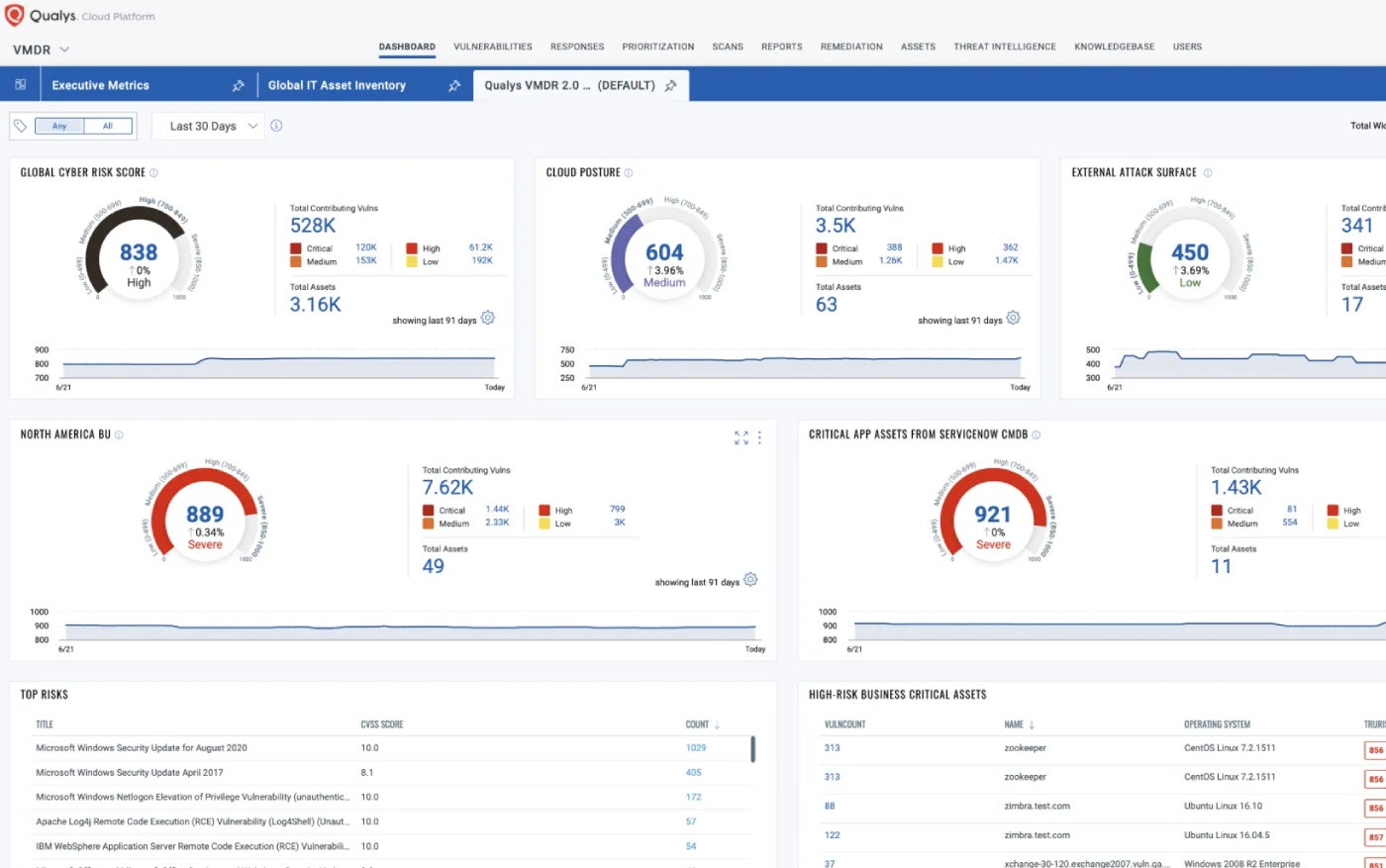
Qualys VMDR: Best for cloud-based enterprises
Qualys Vulnerability Management Detection and Response takes the context of threats under consideration with the intention to prioritize and remediate critical threats all of a sudden. I preferred the worth of its automatic scoring method, referred to as TruRisk.
Why I selected Qualys VMDR
Qualys VMDR does a just right task bringing in combination a collection of key safety purposes, together with vulnerability evaluation, asset discovery, stock control, and assault floor control. It is a part of a big, cloud-based suite of safety merchandise. As such, I imagine it to be a good selection for enterprises and bigger companies working within the cloud.
Pricing
- Qualys pricing gave the impression relatively complicated to me. It is according to the quantity or compute gadgets within the cloud: digital machines, serverless, and container pictures. The unit price varies according to variations within the capability, complexity, and general price proposition of each and every module. The endeavor model of all the suite begins at about $500 monthly and ramps up from there according to the selection of customers. The vulnerability control module is alleged to be to be had to small companies beginning at $250 consistent with yr and $2000 for enterprises.
Features
- Primarily cloud-based however an on-prem non-public cloud equipment is to be had for patrons with strict information sovereignty necessities.
- A cloud-based provider presented essentially to SMEs supplies VMDR at the side of endpoint detection and reaction and patch control gear.
- Risk-based and context-based prioritization of threats
- Integration with patch control, stock control, and ITSM.
- Qualys Threat Research Unit proactively searches for brand new threats by way of examining information from its consumer base, dozens of danger intelligence feeds, third-party information, and the darkish internet.
Pros and cons
| Pros | Cons |
|---|---|
| Broad vary of vulnerability signature databases. | Can be difficult to put in, be informed, and use for much less mature IT retail outlets. |
| Real-time detection of vulnerabilities similar to patches that want to be put in and misconfigurations. | Cloud and hypervisor make stronger may well be stepped forward. |
| Automatically detects the newest superseding patch for the susceptible asset and deploys it. | |
| Qualys is likely one of the marketplace leaders in vulnerability control according to marketplace percentage. |
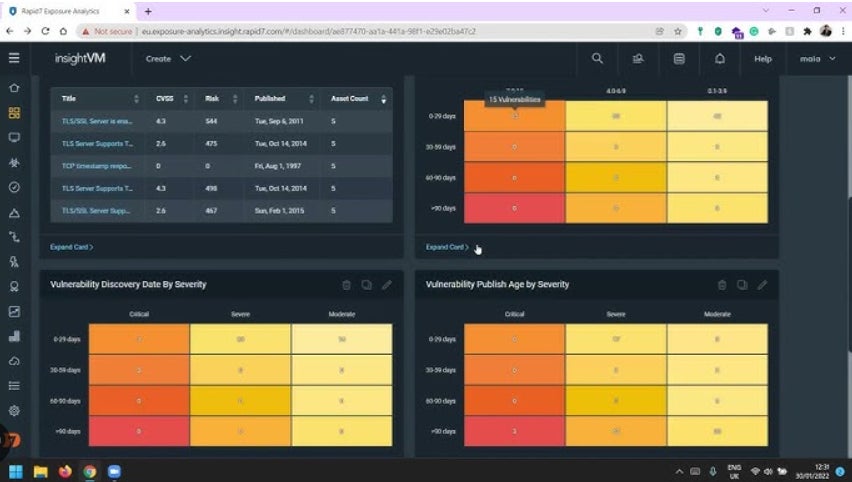
Features
- Continually assesses and prioritizes crucial vulnerabilities the use of threat scoring from 1 to 1000.
- Tracks compliance towards coverage and rules, and compares to trade benchmarks.
- Rapid7 Labs is helping determine all internet-facing property and alert on vulnerabilities.
- Good scanning consistency and vary of units.
Pros and cons
| Pros | Cons |
|---|---|
| Automated remediation. | Best suited for an expert safety groups. |
| Automatic pen-testing. | Can once in a while be sophisticated to arrange. |
| One of the highest vulnerability control distributors consistent with marketplace percentage. | Some customers word integration and deployment problems |
| Runs vulnerability scans throughout cloud, bodily, and digital infrastructure and robotically collects information from all endpoints. | Support responsiveness may well be stepped forward. |
| Security groups can streamline remediation actions similar to vulnerability patching and containment. | |
| Integrates with a spread of third-party gear together with ticketing methods, patch control answers, and SIEM. |
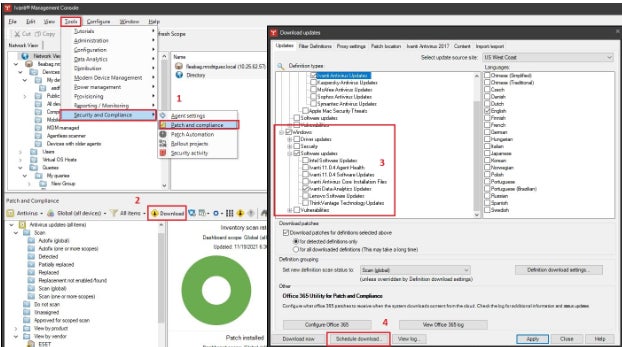
Ivanti VMaaS: Best as a provider providing
Ivanti has a protracted historical past as a best vulnerability control supplier. It gives gear you’ll deploy inside the endeavor or as a provider.
Why I selected Ivanti VMaaS
For me, Ivanti VMaaS stands proud because of its pairing of vulnerability control as-a-service with professional safety analysts, scanning gear, and processes that lend a hand companies determine vulnerabilities at the community and in programs. But the corporate additionally gives best cloud-based gear similar to Ivanti Neurons for risk-based vulnerability control.
Pricing
Features
- Ivanti Neurons for RBVM, can ingest information from a couple of third-party scanners to lend a hand shut gaps and blind spots.
- It robotically analyzes information from vulnerability scanners and gives perception to IT and safety groups.
- Scan findings are robotically correlated and contextualized with danger information and research, and prioritized.
- Finds code weak spot and pinpoints coding mistakes.
Pros and cons
| Pros | Cons |
|---|---|
| This absolutely controlled provider frees up group of workers for different initiatives. | Some customers bitch of loss of make stronger. |
| Easy-to-follow remediation plans. | Customization choices are restricted. |
| Risk scoring guarantees remediation suggestions are concentrated on movements that concentrate on essentially the most critical threats. | Competitive patch control merchandise is also extra complete at finding all endpoints working at the community. |
| Automated workflows. |
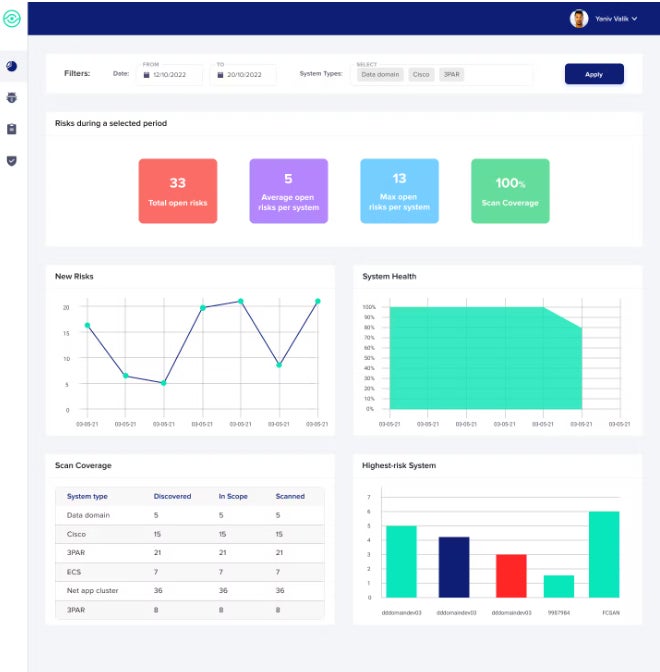
StorageGuard: Best for garage and backup programs
StorageGuard by way of Continuity Software scans, detects, and fixes safety misconfigurations and vulnerabilities throughout loads of garage, backup, and information coverage methods.
Why I selected StorageGuard
Most gear on this information supply wide protection — both throughout all the vulnerability control panorama or are a part of huge safety suites that cross some distance past vulnerability control. I picked StorageGuard because it takes the other manner. It is laser-focused on one side of this marketplace: a complete cope with to a significant hole discovered in lots of vulnerability control merchandise — garage and backup vulnerabilities and misconfigurations. StorageGuard fills that area of interest so neatly that I like to recommend its use along side one of the different gear indexed right here.
Pricing
- $200 monthly for as much as 50 methods.
Features
- Directly addresses the vulnerabilities and possible threats indexed by way of NIST in Security Guidelines for Storage Infrastructure.
- Broad protection of garage and backup apps and methods from the likes of Dell, NetApp, Hitachi Vantara, Pure, Rubrik, Commvault, Veritas, HPE, Brocade, Cisco, Veeam, Cohesity, IBM, Infinidat, VMware, AWS, and Azure.
- Can discover deviation from a designated configuration baseline.
Pros and cons
| Pros | Cons |
|---|---|
| Scans and reveals weaknesses in garage and backup programs that different scanners pass over. | Does now not cope with conventional vulnerabilities in 1/3 get together programs and OSes. |
| Users touch upon ease of use and thoroughness to find backup and garage misconfigurations. | Focused basically on discovery of problems versus solution. |
| Provides evidence of audit compliance towards CIS Controls, NIST, ISO, PCI, NERC CIP, and others. |
Vulnerability control: Frequently requested questions
What are vulnerability control gear?
According to NIST, vulnerability control is a “capability that identifies vulnerabilities [common vulnerabilities and exposures] on devices that are likely to be used by attackers to compromise a device and use it as a platform from which to extend compromise to the network.”
As neatly as mitigating configuration or code problems that would possibly permit an attacker to take advantage of an atmosphere, the definition is ceaselessly broadened to incorporate patch control, MDM, IT asset control, and EDR. The vulnerability control serve as is ceaselessly built-in into a big safety suite.
How do vulnerability control gear paintings?
Vulnerability control can also be damaged into a sequence of steps, a lot of which are actually automatic:
- Vulnerability scanning.
- Reporting on any vulnerabilities found out and prioritization according to their possible have an effect on at the trade.
- Deployment of remediation or advice of remediation steps.
- Validation of remediations to make sure problems had been resolved.
- Reporting at the state of vulnerabilities and their solution inside the endeavor.
How are vulnerability control gear deployed?
They can also be deployed as on-premises instrument, delivered as SaaS, or as controlled products and services.
What is vulnerability control as a provider?
Vulnerability control as a controlled provider is delivered by way of a supplier by means of the cloud relatively than downloading and working on-prem instrument. It frequently identifies, assesses, studies, and manages vulnerabilities throughout cloud identities, workloads, platform configurations, and infrastructure.
What options must I search for in a best vulnerability control instrument?
Certain core purposes are found in all best vulnerability control platforms. These come with:
- Discovery of all units, programs, and methods and detection of possible vulnerabilities and misconfigurations that can exist anyplace inside the community on any software that connects to the community.
- A database of vulnerabilities and threats this is frequently up to date.
- Integration with a variety of platforms, safety methods, vulnerability scanners, ticketing methods, and different safety gear.
- A technique of threat scoring and prioritization.
- Automatic remediation or remediation steering.
- Reporting functions that spotlight problems and compliance.
How do I make a selection the most productive vulnerability control instrument for my trade?
Those searching for a vulnerability control instrument must ask questions similar to:
- What platforms does the instrument function on? Be conscious that some are concentrated on Linux, some on Windows, and a few quilt a couple of or all OS and platforms. Also consider what body of workers are already educated on. Don’t upload Linux gear in case your inner group of workers are educated on Windows, and vice-versa.
- What endpoints are lined? Some deal basically with servers, PCs, and laptops, whilst others lengthen to smartphones, IoT, wi-fi, and different units.
- Which portions of the protection panorama are you taking a look so as to add or improve past vulnerability control? If you’re in the middle of an entire overhaul of your whole safety infrastructure, get started with the suite after which to find one that comes with the vulnerability control options you wish to have. But if you have already got a cast safety spine, center of attention on vulnerability control gear that give you the protection you wish to have.
- Pay consideration to the advantageous print in contrasts and glance carefully at price construction, the potential of further charges, make stronger prices, and so forth.
- Don’t be caught on one supplier for all safety wishes. Vendor A might paintings for many of your safety infrastructure, however Vendor B is also higher at vulnerability control.
- What do analysts similar to Gartner say concerning the other gear, their marketplace percentage, their professionals and cons, and long run route?
Whatever instrument you make a choice from the record above, the advantages of vulnerability control briefly display up when it comes to fewer breaches, information this is higher safeguarded, assaults being noticed some distance previous than earlier than, and added automation.
Methodology
The gear lined right here had been decided on according to analyst studies, peer evaluations, and consumer pride, in addition to evaluations posted in roosho and different Technology Advice websites. I additionally equipped a mixture of full-fledged vulnerability control merchandise, extremely specialised gear, and the ones the place vulnerability control is one module inside of a miles greater suite.













No Comment! Be the first one.