A passkey is a selected authentication manner that can be utilized as regularly as a password however to supply further safety. Passkeys vary from passwords as they mix personal and public cryptographic keys to authenticate customers, while a password depends on a selected selection of characters.
According to Google, probably the most rapid advantages of passkeys are that they’re phishing-resistant and spare other folks the headache of remembering numbers and particular characters in passwords.
As passwordless authentication continues to adapt — in accordance with phishing-related dangers — believe the use of passkeys to enforce an added layer of safety to offer protection to your on-line accounts and knowledge.
This article will outline passkey generation, discover the way it works, and talk about the added safety advantages of the use of a passkey.
What is a passkey?
A passkey refers to a code or a sequence of characters used to achieve get entry to to a secured gadget, software, community, or provider. Passkeys are incessantly used along with usernames or person IDs to create two-factor authentication.
SEE: How to Create an Effective Cybersecurity Awareness Program (roosho Premium)
After you’ve established a passkey, all you wish to have to do is log in to finish the authentication procedure, usually the use of biometric information similar to a fingerprint or facial reputation. For those that make the most of a passkey, logging in turns into a easy, just about automated procedure; for malicious actors, it turns into just about inconceivable.
The implementation of passkeys is extremely adaptable since they is also configured to be cloud-synced or hardware-bound, contingent at the person’s possible choices in regards to the specific software, provider, or software.
How do passkeys paintings?
When logging in for the primary time, a person who desires to get entry to an app or site with passkey generation — similar to NordPass — can be requested to generate an unique passkey. This passkey, which can be required for authentication one day, will also be accessed the use of both biometrics or private PINs according to the person’s variety and the features in their most well-liked software.
Figure A
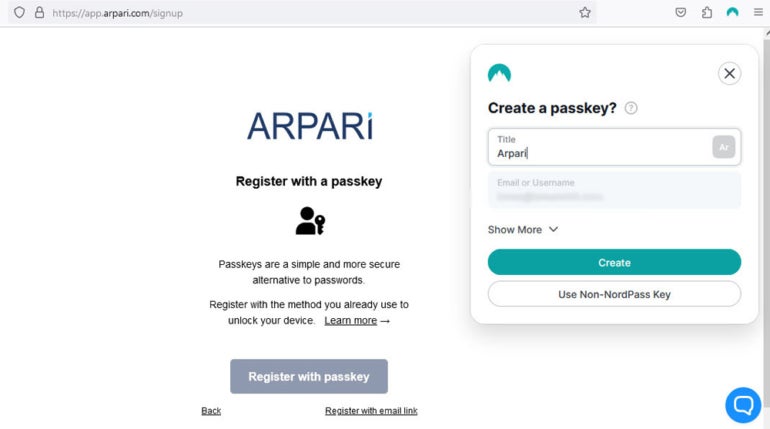
During this level, two mathematically related cryptographic keys are generated: a public key that remains with the site, provider, or software however is attached to the account, and a personal key that remains at the person’s {hardware} or cloud account.
How do you check in with a passkey as an alternative of a password?
Passkey authentication is finished within the background, making login at the person’s finish seamless — with simply the press of a button.
Figure B
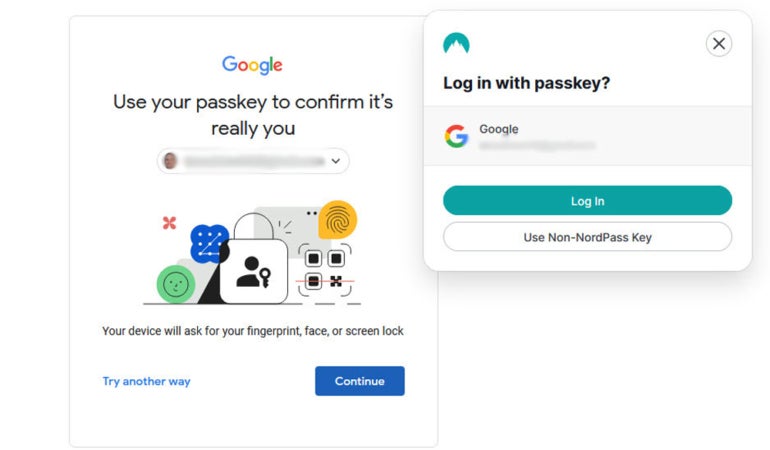
The provider or software will ship a randomly generated “challenge” to the person’s software throughout logins, which the person will have to react to by means of signing in with the non-public key.
SEE: Passkey Adoption Is Accelerating in APAC — Except for Australia (roosho)
The app or site can verify the legitimacy of the non-public key through the use of the corresponding public key to substantiate the reaction. Access is permitted, and authentication is validated if the person’s verified signature connected to the problem’s reaction is of the same opinion with the unique randomly generated problem; if now not, get entry to is denied.
How are passkeys other from passwords?
The most crucial variations between passkeys and passwords come with:
- Passwords will also be illicitly acquired thru brute-force hacking, social engineering, and knowledge breaches, while passkeys are harder (even though now not inconceivable) to thieve. Hackers would wish to bodily thieve your software or breach your cloud account and wager your PIN or give you the chance to avoid your biometric authenticator.
- Secure password utilization calls for customers to generate and take into account many advanced credentials or make use of a password supervisor, which has its personal demanding situations and dangers. Passkeys routinely authenticate customers with their software’s free up mechanisms, making them a lot more practical and extra handy to make use of.
- Passwords can be utilized throughout any software with none further setup, however passkeys are in most cases certain to precise {hardware}. A cloud-based passkey resolution would possibly paintings throughout more than one units, however customers must remember that their personal keys can be saved on any individual else’s servers as an alternative of in the community.
What are some great benefits of the use of a passkey?
- Unique logins: A password is reused each time you log in to a specific account, which means that any malicious actor who will get their fingers on it’s going to have unfettered get entry to. Passkeys, then again, use cryptographic key pair generation to create distinctive authentication credentials for each login, giving hackers not anything to “guess” or thieve. Passkeys are proof against brute drive assaults and social engineering strategies like phishing, plus they are able to’t be uncovered in an information breach.
- Added safety layer: Passkeys use your software’s authenticator, similar to a biometric login or PIN code, as a type of integrated 2FA that protects your account. Whether your personal key’s saved in the community for your software or within the cloud, a would-be hacker would wish to authenticate along with your software ahead of having access to it and compromising your account.
- User comfort: Passkeys don’t wish to be memorized or periodically modified, and logging in with them calls for a unmarried button press, offering a a lot more streamlined revel in than passwords. And, as I simply discussed, they come with 2FA to higher give protection to accounts, however they don’t require customers to supply secondary authentication for each and every particular person login — if you’ve logged into your software, that authentication is carried out to each account you get entry to that consultation.
What units have compatibility with passkeys?
Many units from the preferred tech producers have compatibility with passkeys. Passkey generation was once advanced consistent with W3C and FIDO Alliance requirements to help in compatibility, and the massive 3 software producers (Apple, Google, and Microsoft), in addition to all primary internet browsers, already make stronger it.
Can passkeys be shared?
The implementation of passkey generation remains to be growing, however some corporations have discussed the potential of credential sharing among customers — so long as the true passkeys are saved secure within the cloud and out of the fingers of doable hackers. Since sharing account get entry to with circle of relatives, buddies, and coworkers is an easy and fast procedure, this option would possibly enhance the whole person revel in. However, it’s nonetheless unclear how this serve as will also be securely controlled in a trade surroundings.
SEE: How to Use Google’s Titan Security Keys With Passkey Support (roosho)
Another a very powerful aspect to believe is whether or not companies must turn into much more depending on cloud suppliers and surrender much more possession and regulate over credential control, for the reason that a breach of the ones events’ information would, indubitably, have disastrous penalties.
Hardware-bound passkeys, versus cloud-based passkeys, are saved on safety keys, bodily {hardware} authenticators, or specialised {hardware} built-in into laptops and desktops. This implies that the passkey is neither transferable nor duplicated. Hardware-bound passkeys will also be an alternate for organizations short of to stop staff from copying or sharing keys throughout units.
Are passkeys extra safe than passwords?
Generally talking, passkeys are extra safe than passwords. However, their safety depends upon more than a few components, together with the power of the cryptographic strategies used to encrypt private and non-private keys, the safety of the software’s authenticator, and the trustworthiness of the passkey resolution supplier.
SEE: Nearly 10 Billion Passwords Leaked in Biggest Compilation of All Time (roosho)
Users can take steps to make passkeys extra safe, alternatively. For instance, passkeys use your software credentials as a 2d type of authentication, so the use of biometric login as an alternative of a PIN can spice up the safety of your personal key. Minimizing cookie assortment and periodically clearing cached credentials also are excellent practices for making improvements to general internet safety. It’s additionally vital to counterpoint passkeys with different safety equipment and controls, similar to encrypted onerous drives, software malware coverage, and firewalls.
Can a passkey be hacked?
Yes, passkeys will also be hacked, however it’s a lot more tricky than stealing a password. As I’ve described above, passkeys are safe by means of more than one layers of safety, together with native software authentication and powerful encryption. Simply obtaining the non-public key isn’t sufficient as a result of, even with cloud-based passkey answers, you wish to have to authenticate with the native software ahead of you’ll be able to get entry to any on-line accounts.
Will passkeys substitute passwords and password managers?
In my opinion, passkeys will ultimately substitute passwords and password managers, even though the transition is lately nonetheless to start with levels. As passkey generation improves and extra companies undertake it, we’ll most likely see passwords section out even among house customers.
What is the way forward for passkeys in generation?
Right now, many of the inventions in passkey generation are — as it should be, individually — enthusiastic about options, that are extra handy for builders and companies to make use of within the hopes of using adoption.
For instance, at this time, passkeys created in a single ecosystem don’t simply paintings with others. So, if a person creates a passkey the use of their iPhone, it’s tricky, if now not inconceivable, to make use of the similar passkey on a Windows computer or to switch all in their passkeys from one surroundings to some other.
This limitation, alternatively, simplest in reality applies to the environment-native passkey equipment that include more moderen Apple, Windows, and Android units. As extra third-party passkey suppliers input the marketplace, the usual is starting to shift towards cross-platform make stronger and more uncomplicated portability to enhance the client revel in.






No Comment! Be the first one.